2023春秋杯春季赛
本文最后更新于:2023年10月7日 晚上
MISC
sudo
CVE-2023-22809
连接靶机执行sudo -V,发现版本为1.8.21p2符合文章中说的版本
查看/etc/sudoers发现当前文件可以无密码执行sudoedit /etc/GAMELAB,这也符合文章中的条件
文章中执行了一条EDITOR="vim -- /path/to/extra/file" sudoedit /etc/GAMELAB,用来编辑文件
那么我们改一下EDITOR="cat -- /flag" sudoedit /etc/GAMELAB就可以读取/flag文件获得flag
piphack
编写setup.py
1 | |
在github中创建仓库,上传setup.py,然后连接靶机输入git+https://github.com/xxx/xx.git,靶机就会自动下载仓库中的文件,并执行setup.py,只要靶机将仓库下载下来,flag就会在出现报错信息中
wordle
连接靶机之后先随便输入几个五个字母的单词,然后将存在错误的字母的单词排除,将正确的字母在正确的位置的单词保留,之后就可以得到正确的单词
58与64
下载附件解压之后,得到很多txt文件,而txt文件中基本上只有一两个字母,根据题目中的58,猜测文件内容为base58
将文件内容进行base58解密之后连接起来得到base64字符串,进行多次base64解密得到flag
1 | |
盲人隐藏了起来
解压附件得到三个文件12,34.mp4,flag.zip,使用010打开12,34.mp4
发现12文件中的内容,与34.mp4中mdat段的内容结构类似,将12中的内容替换为34.mp4中的mdat段之后,打开视频得到压缩包密码ChunJiSai7k7kbibi@!
解压得到了flag.png,在文件结尾存在字符串keyischunqiu123不过没有发现有什么用,执行zsteg -a flag.png,发现在b1,bgr,lsb,xy中存在flag信息,使用zsteg flag.png -e b1,bgr,lsb,xy |strings | grep flag得到flag
happy2forensics
在http数据包中,发现有主机使用POST方法像服务器上传了一个secret.rar,导出之后解压得到secret.vhdx,装载之后发现是bitlocker加密的磁盘文件,在数据包中,存在一个主机使用20端口向80端口发送数据,因为20端口一半用于FTP-DATA协议,而且主机只发送syn数据包,不进行tcp连接,查看数据包之后发现tcp.seq_raw字段中可能存在数据
使用tshark导出数据tshark -r happy2forensics.pcapng -Y "tcp.srcport==20" -T fields -e tcp.seq_raw,将导出数据转换为字符串之后得到bitlocker:120483-350966-299189-055297-225478-133463-431684-359403
装载磁盘文件,存在很多图片,同时还存在一个210-1.png无法直接打开,使用010查看之后发现存在多个文件,使用foremost分离文件,同时在磁盘文件中作为回收站的区域中存在一个压缩包,压缩包中存在flag2.txt
下面是jpg文件内容
根据提示合并磁盘文件中的png图片,与210-1.png分离之后得到的png图片
1 | |
210-1.png合并图片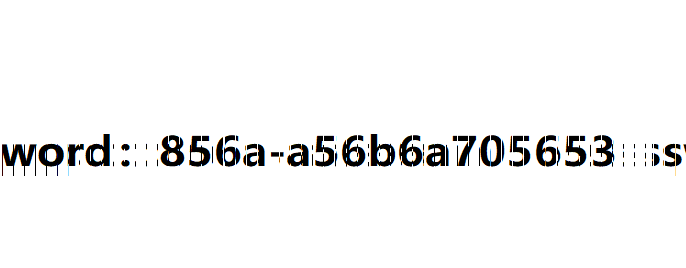
解压压缩包得到flag2:-919c-a140d7054ac5
磁盘文件合并图片
看来flag并不在这里
使用010查看之前分离出来的jpg,发现存在两个jpg头,删除开始的jpg头之后得到一张新的图片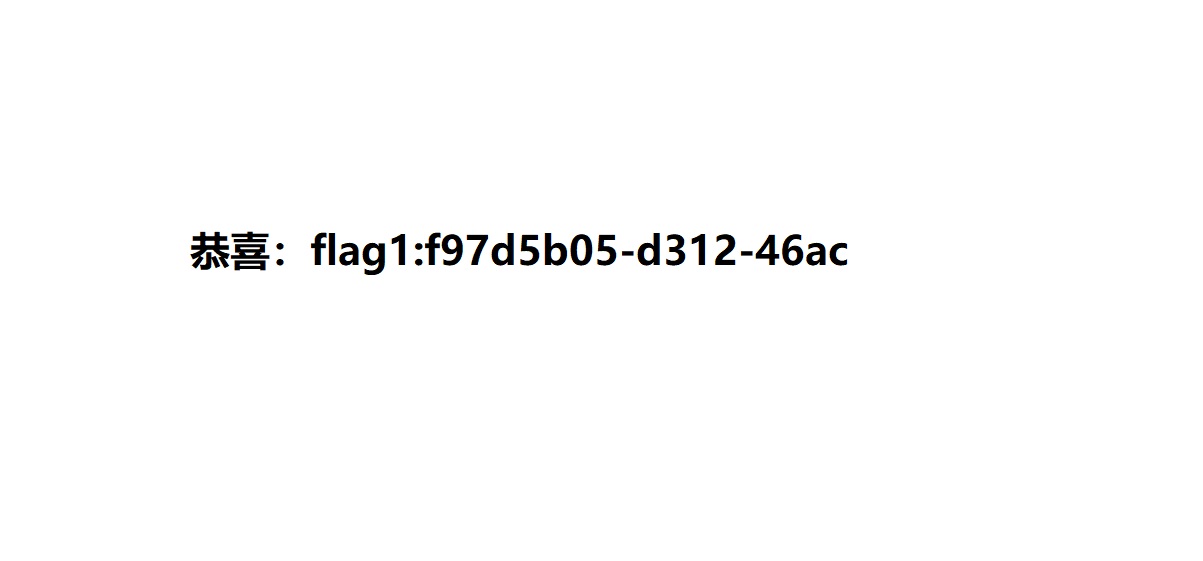
REVERSE
sum
因为输入的数据会写入到一个9x9的二维数组中,同时二维数组的内容为0~9的数字,并且,输入的数据会替换掉二维数组中0所在的位置,所以我猜测是一个数独游戏,将matrix变量的内容导出来,作为一个9x9的方阵
将数字导入到这个数独网站之后就可以获得数独中需要填入的内容了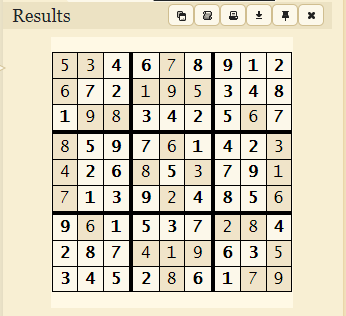
Pytrans
先使用pyinstxtractor将exe解包,然后使用在线pyc反编译网站,将解包之后得到的run.pyc反编译
1 | |
反编译失败,不过我们可以通过run.pyc中的字符串内容,来推测实际代码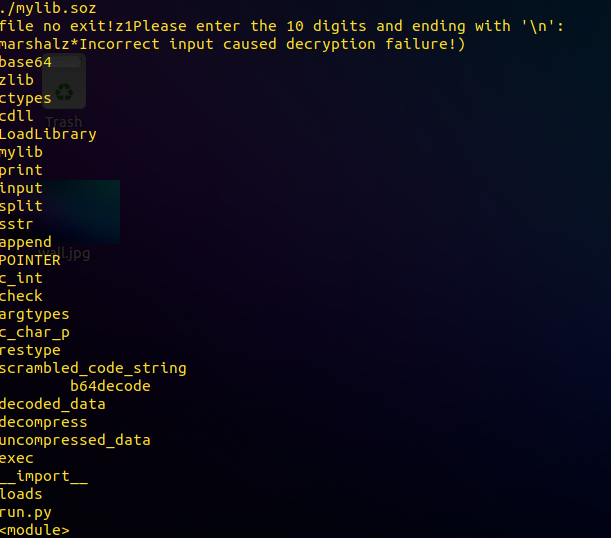
1 | |
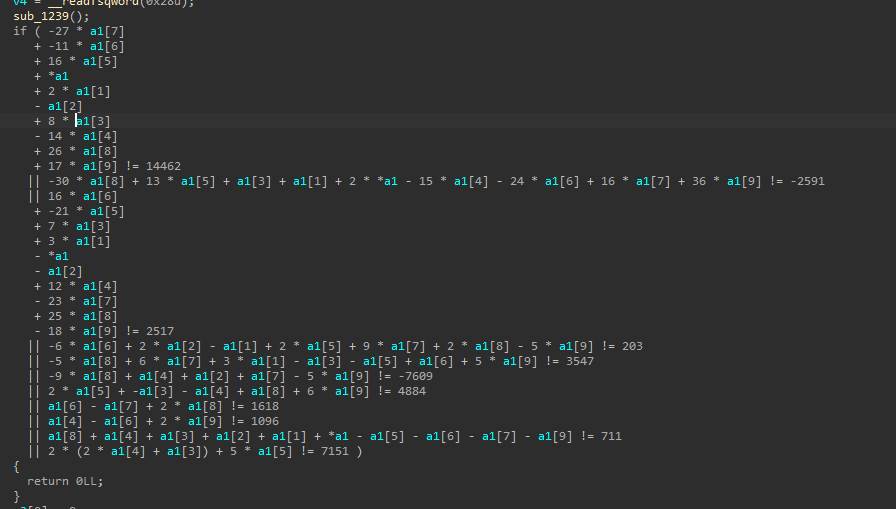
在mylib.so中的check函数的开头存在这段代码,使用python的z3模块解方程得到数据内容
1 | |
使用010查看导出的data文件,发现是pyc文件缺少了头,因为exe解包之后的pyc中大多数都是python3.8版本的pyc文件,所以将3.8版本的pyc头写入data文件之后,进行反编译
1 | |
发现将上面脚本中得到的e中的整数,转换为十位二进制之后可以得到一个迷宫,通过解迷宫之后输入可以得到flag
迷宫路径为sddsdssdddwwwddsssssaaaaassddsddwdds
Emoji Connect
执行解压之后得到的.vsto文件会在excel中安装com程序,之后创建一个新的表格,在excel的菜单栏中会出现一个春秋GAME,点击之后可以开启一个连连看游戏,这个vsto文件实际上是将Emoji_Connect.dll安装到excel中,不过我第一次安装成功了,但删除之后再安装菜单栏中就没有春秋GAME了Emoji_Connect.dll是一个.net程序,使用dnspy分析程序
1 | |
1 | |
PWN
p2048
1 | |
1 | |
1 | |
babygame
当获得了足够多的分数时就可以构造足够多次数的格式化字符串,以修改某个地址处的数据
1 | |
sigin_shellcode
在useful_tools中已经将a0寄存器设置为指向"/bin/sh"的指针了,并且已经将shellcode中的后八位设置为执行execve系统调用的代码了,不过a1与a2寄存器没有清空,所以这是我们需要做的
1 | |
easy_LzhiFTP
在touch时存在数组越界,当创建第17个成员时会将第1个成员设置为第17个成员的size,可以做到任意地址读写
1 | |