2022西湖论剑-初赛
本文最后更新于:2023年10月15日 晚上
Reverse
BabyRE
程序先对输入的数据进行base8加密,并将加密后数据的0x10~0x70与16230465152334621443147115031070150320711603206314033466154344611443406614230466156344661543046比较
然后对加密后数据的0~0x70进行魔改过的sha1加密,并将哈希值与67339fc92b4875b8c073c76994ef1ca4ce632d26比较
最后将输入数据的0x2a~0x30作为密钥,对base8加密后数据的前0x70个字节进行rc4加密
1 | |
Pwn
Message Board
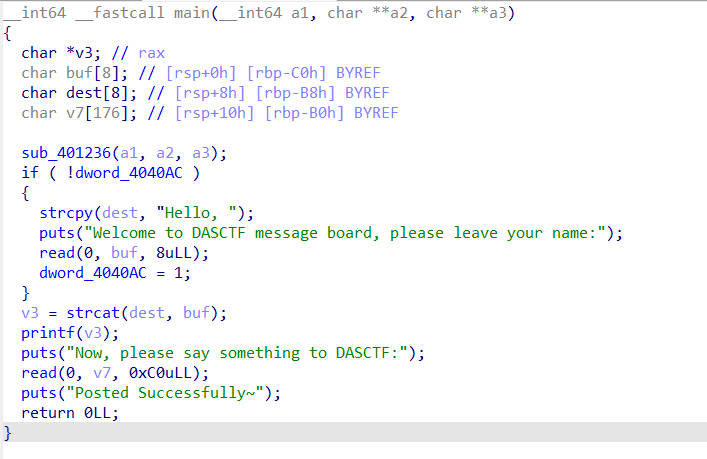
main函数中存在栈溢出,但只能溢出0x10个字节,只能修改rbp与rip的值,所以需要进行栈迁移
1 | |
babycalc
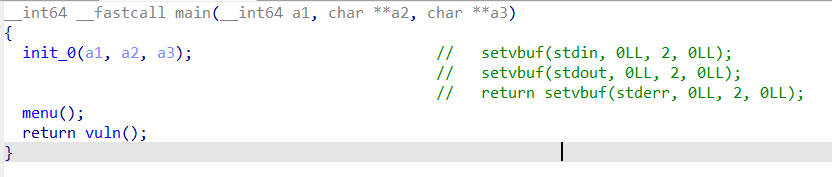
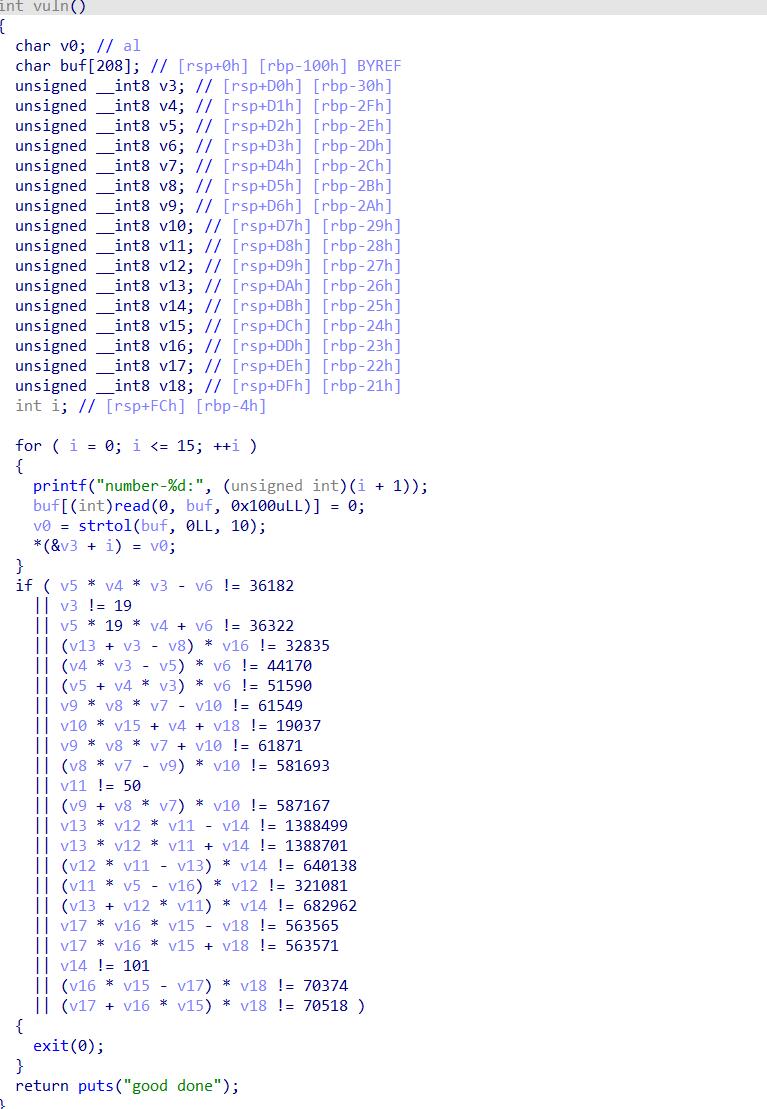
vuln函数中可以向buf变量中写入0x100字节的数据,这里可以修改i的值,导致下面*(&v3+i)索引到其他地址处,并且当输入0x100字节的数据时,会将leave恢复的rbp的值的最低字节变成0x00,在溢出之前,还需要通过验证
如果恢复的rbp的最低字节变成0x00时,恢复的rbp刚好位于vuln函数的栈空间中,这时执行一个leave;ret,就可以执行我们构造好的rop链,但这种情况属于偶然的,所以需要进行爆破
1 | |
1 | |
Misc
take_the_zip_easy
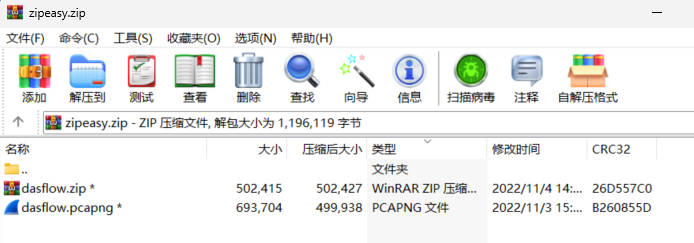
题目给了一个zipeasy.zip文件,里面有两个文件都是真加密,那么只能爆破密码了,但是如果单纯的爆破的话,需要很长时间才可能成功,不过zipeasy.zip中有一个dasflow.zip,这个文件中有部分字节是已知的,所以可以通过bkcrack进行明文爆破
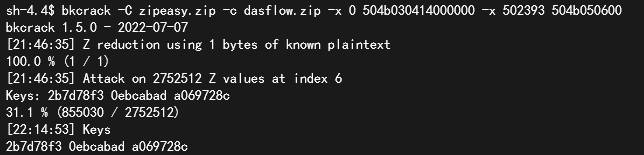
因为知道的信息较少,所以爆破的时间比较长,在爆破的时候可以爆破两次
一次猜测dasflow.zip不是加密压缩包,那么命令就是bkcrack -C zipeasy.zip -c dasflow.zip -x 0 504b030414000000 -x 502393 504b050600
另一次猜测dasflow.zip是加密压缩包,那么命令就是bkcrack -C zipeasy.zip -c dasflow.zip -x 0 504b030414000100 -x 502393 504b050600
从结果来看,dasflow.zip不是加密的压缩包,爆破之后获得的key为2b7d78f3 0ebcabad a069728c
执行bkcrack -C zipeasy.zip -c dasflow.zip -k 2b7d78f3 0ebcabad a069728c -d dasflow.zip导出dasflow.zip,解压之后是dasflow.pcapng
分析数据包中的http数据,发现上传了一个eval.php
1 | |
1 | |
使用命令tshark -r dasflow.pcapng -T fields -e text -Y "http contains eval.php or http contains PHPSESSID"获取恶意用户发送和服务器返回的数据
1 | |
从命令中发现,服务器中存在flag文件,恶意用户对其进行了加密压缩,解压缩密码为airDAS1231qaSW@,压缩包文件为flag.zip,从数据包中找到并导出flag.zip,解压缩之后获得flag
机你太美
npbk文件是夜神模拟器的备份文件,导入文件创建模拟器,开机之后发现存在密码,使用adb连接模拟器,进入/data/system目录,删除locksettings.db文件之后重启模拟器,发现不需要密码了
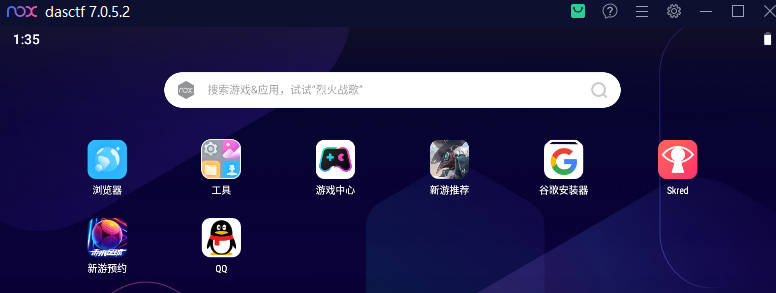
模拟器中除去自带的软件之外,安装了QQ和Skred,QQ是登不进去的,从Skred中发现了通信的记录,记录中一个备注为bbb的人向模拟器发送了多个压缩包和两张图片
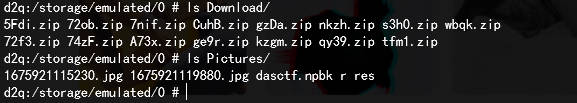
所有的压缩包都带有密码,那只能先从两张图片中找线索了
从1675921115230.jpg的A2通道中发现数据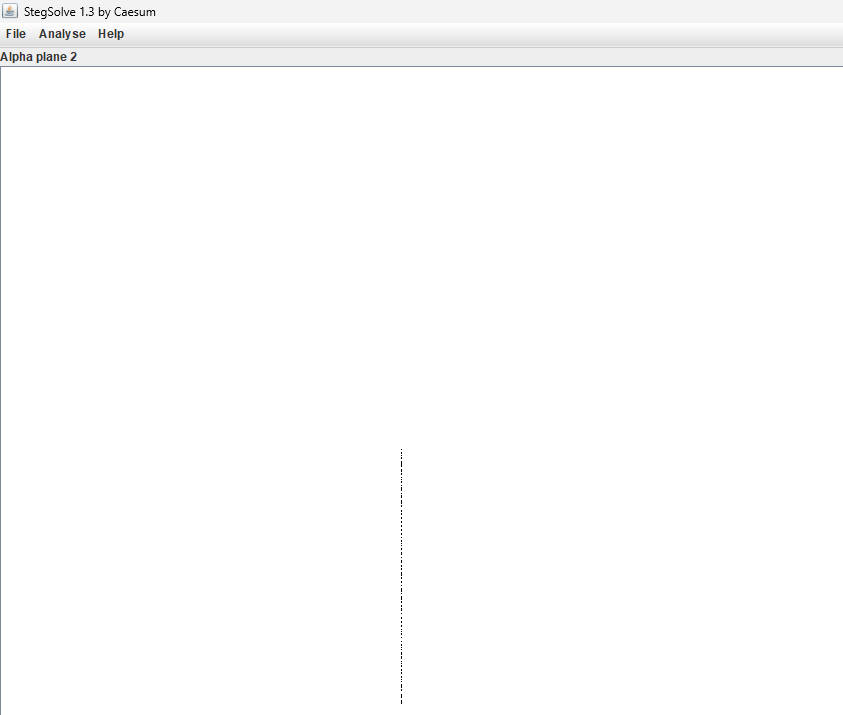
1 | |
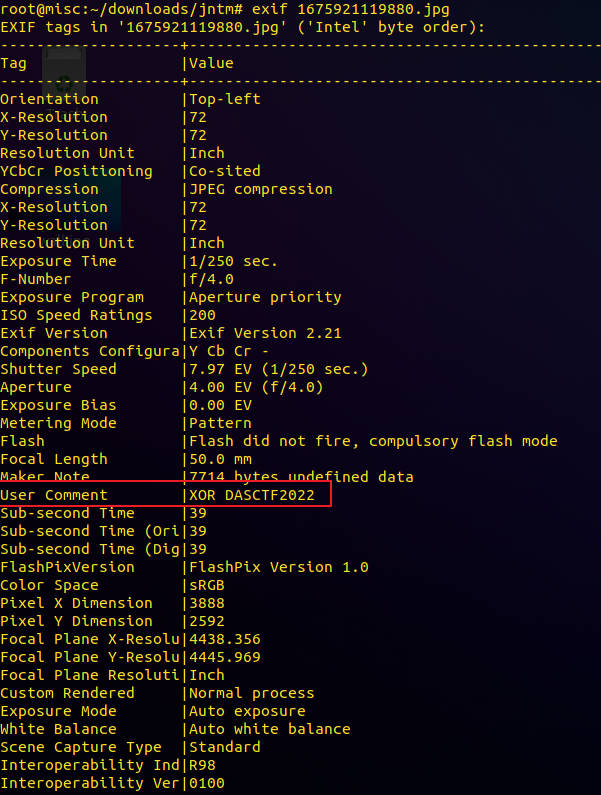
查看另一张图片的exif信息发现,在User Comment中提示需要异或DASCTF2022
1 | |