2021金砖-pwn
本文最后更新于:2023年10月15日 晚上
pmagic1
1 | |
pwn2
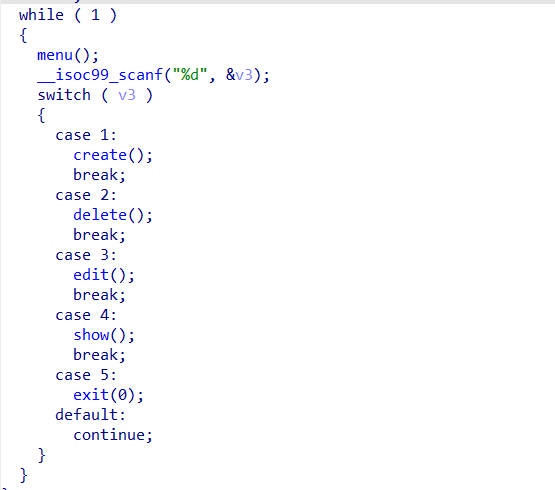
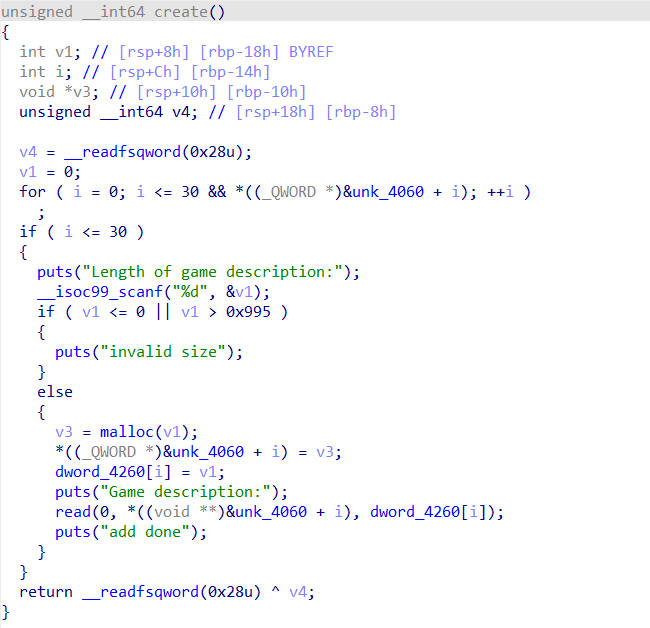
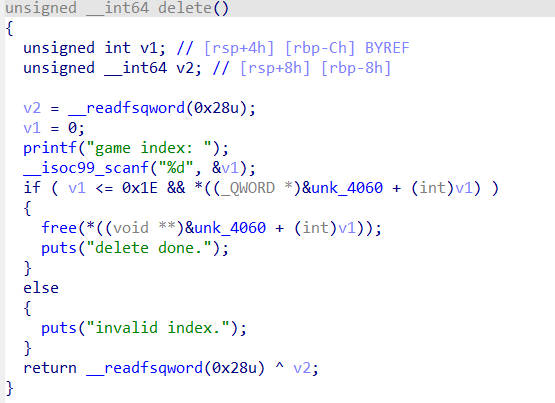
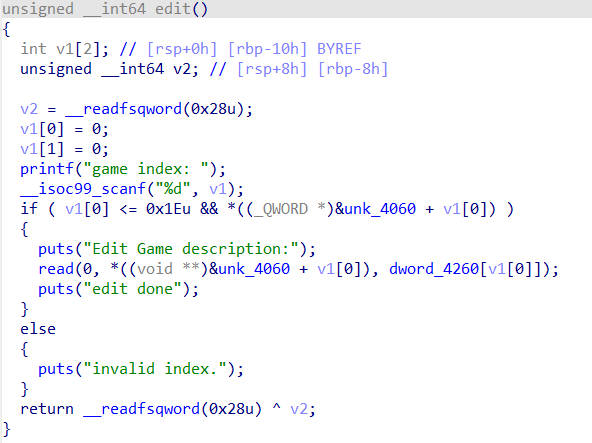
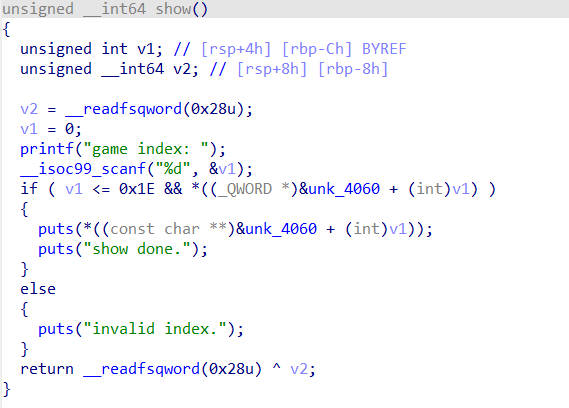
delete函数中存在UAF,且create函数中可以创建较大的chunk,所以获取libc地址很简单,但是程序禁用了execve系统调用,所以需要使用orw获取flag
1 | |
pwn3
启动脚本分析
1 | |
1 | |
分析
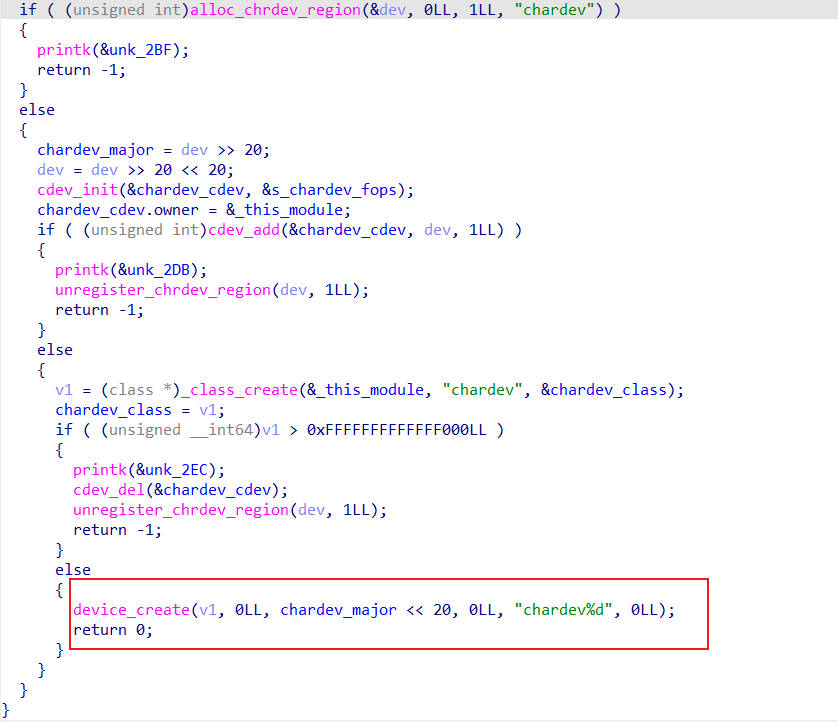
这里注册了一个设备
chardev,并且会在/dev目录下创建名为chardev0的设备
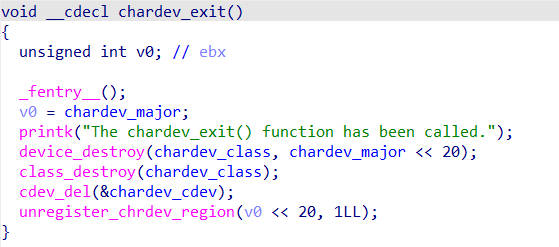
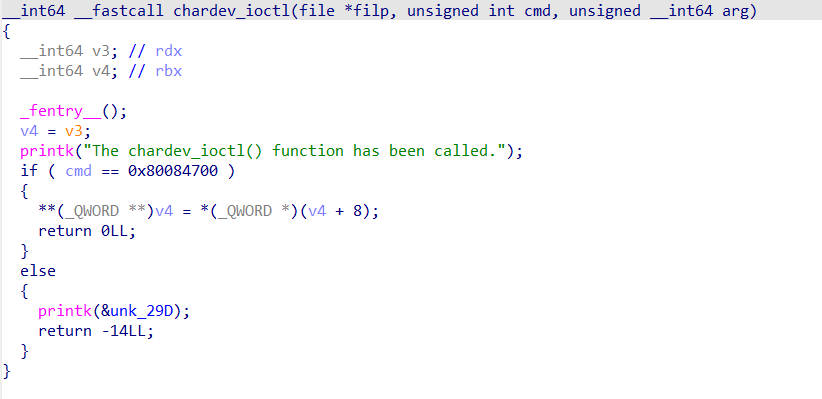
当我们对打开的/dev/chardev的文件句柄进行ioctl操作时会执行这个函数
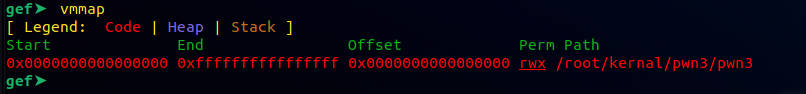
可以看到内核中的地址都是可读可写可执行的,而在chardev_ioctl函数中,存在任意地址写入,而且每次开启内核中的地址都不变,那么可以修改chardev_ioctl函数中else部分的代码为commit_creds(prepare_kernel_cred(0)),然后正常返回,之后在用户态调用system("/bin/sh");就可以查看flag文件了
1 | |
2021金砖-pwn
https://rot-will.github.io/page/wp/2021金砖-pwn/